Remote IoT Access: Android, Routers & Security - A Guide
Can you truly harness the power of the Internet of Things (IoT) from anywhere, at any time? The ability to remotely access and manage your IoT devices, especially those tucked behind routers and firewalls, is no longer a futuristic concept; it's a fundamental requirement for efficiency, security, and even survival in the interconnected digital landscape.
The modern world is awash in smart devices, from the humble smart thermostat to complex industrial machinery. These devices, designed to gather data, automate processes, and enhance our lives, are rapidly becoming integral to our daily routines and business operations. However, the true potential of these devices is unlocked only when we can access and control them remotely. This is where the intricacies of remote access to IoT devices come into play, and understanding how it works is more critical now than ever before.
The core principle behind remote access IoT is remarkably straightforward: establishing a secure pathway for communication between your IoT device, typically residing on a private network, and an external device, such as your Android smartphone or a web-based platform. Think of it as creating a secret tunnel through which you can send commands, receive data, and troubleshoot problems without being physically present.
- Antonio Aguilar Jr Biography Of The Mexican Singer Actor
- Ainsley Earhardt Age Birthday More Latest Updates
| Aspect | Details |
|---|---|
| Concept: | Enabling control, monitoring, and data retrieval from IoT devices located remotely, often behind routers and firewalls. |
| Applications: | Smart home automation, industrial monitoring, remote diagnostics, environmental sensing, fleet management. |
| Challenges: | Network security, firewall configurations, NAT traversal, device discoverability, ensuring data integrity and privacy. |
| Technologies: | VPNs (SSL/TLS, DTLS), SSH tunnels, Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), secure cloud platforms (e.g., SocketXP). |
| Benefits: | Enhanced convenience, improved efficiency, increased security (with proper implementation), cost reduction (e.g., reduced need for on-site technicians). |
| Security Measures: | Robust encryption (TLS/DTLS), firewall configuration (allowing only required traffic), VPN connections for secure access, regular security audits and updates. |
| Example Tools: | SocketXP, VNC Connect, TeamViewer, SSH clients (e.g., Termius), cloud-based IoT platforms. |
| Importance: | Remote access is a necessity for control, monitoring, data gathering. |
| Real-world example: | Remote access to Raspberry Pi, embedded devices, or android devices. |
| Additional Tools: | Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC). |
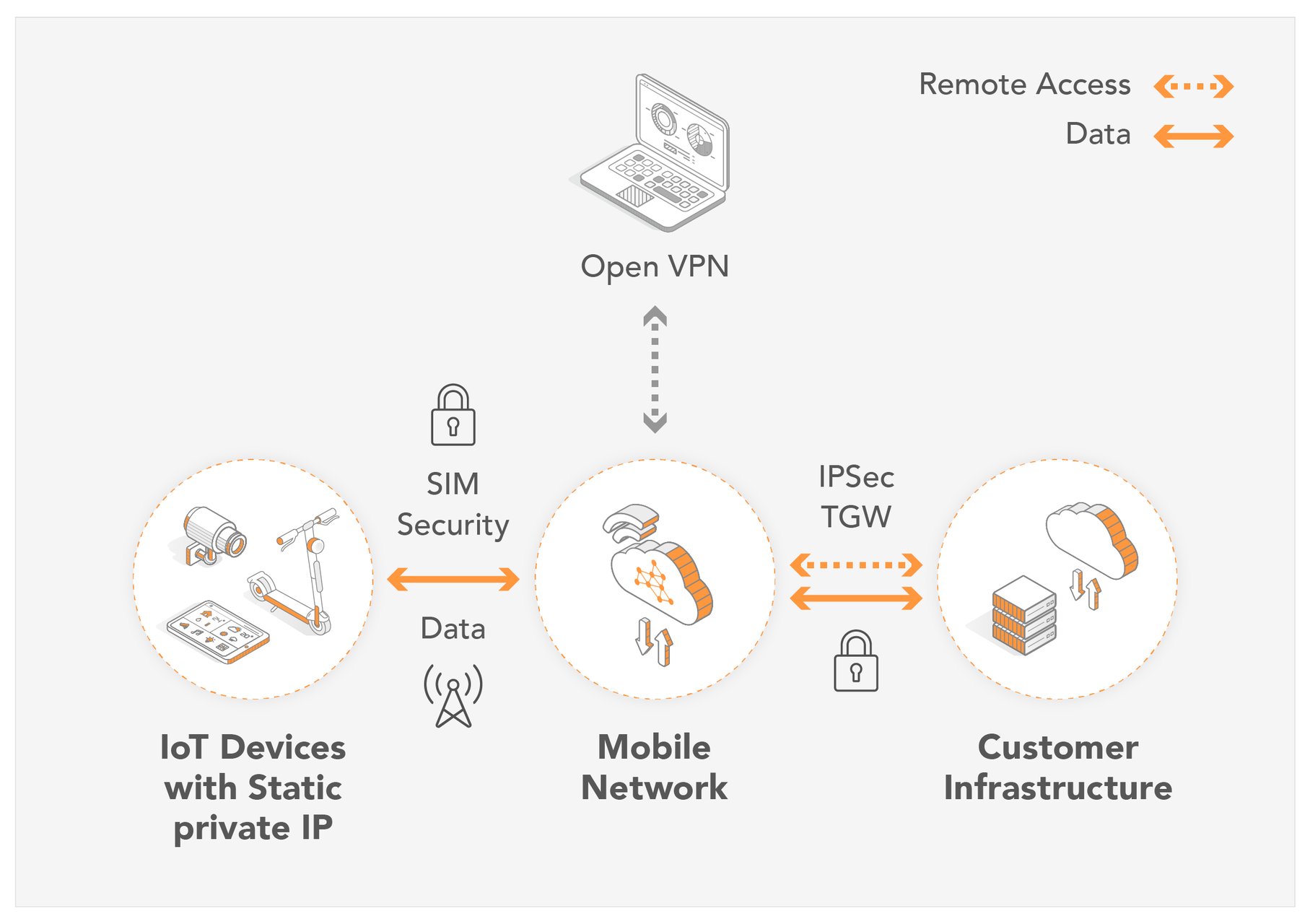
One of the primary hurdles is navigating the complexities of firewalls and Network Address Translation (NAT), which are designed to protect private networks from external threats. Firewalls block incoming traffic by default, making it difficult to initiate connections to devices within the network. NAT, on the other hand, translates private IP addresses to a public IP address, further complicating direct access.
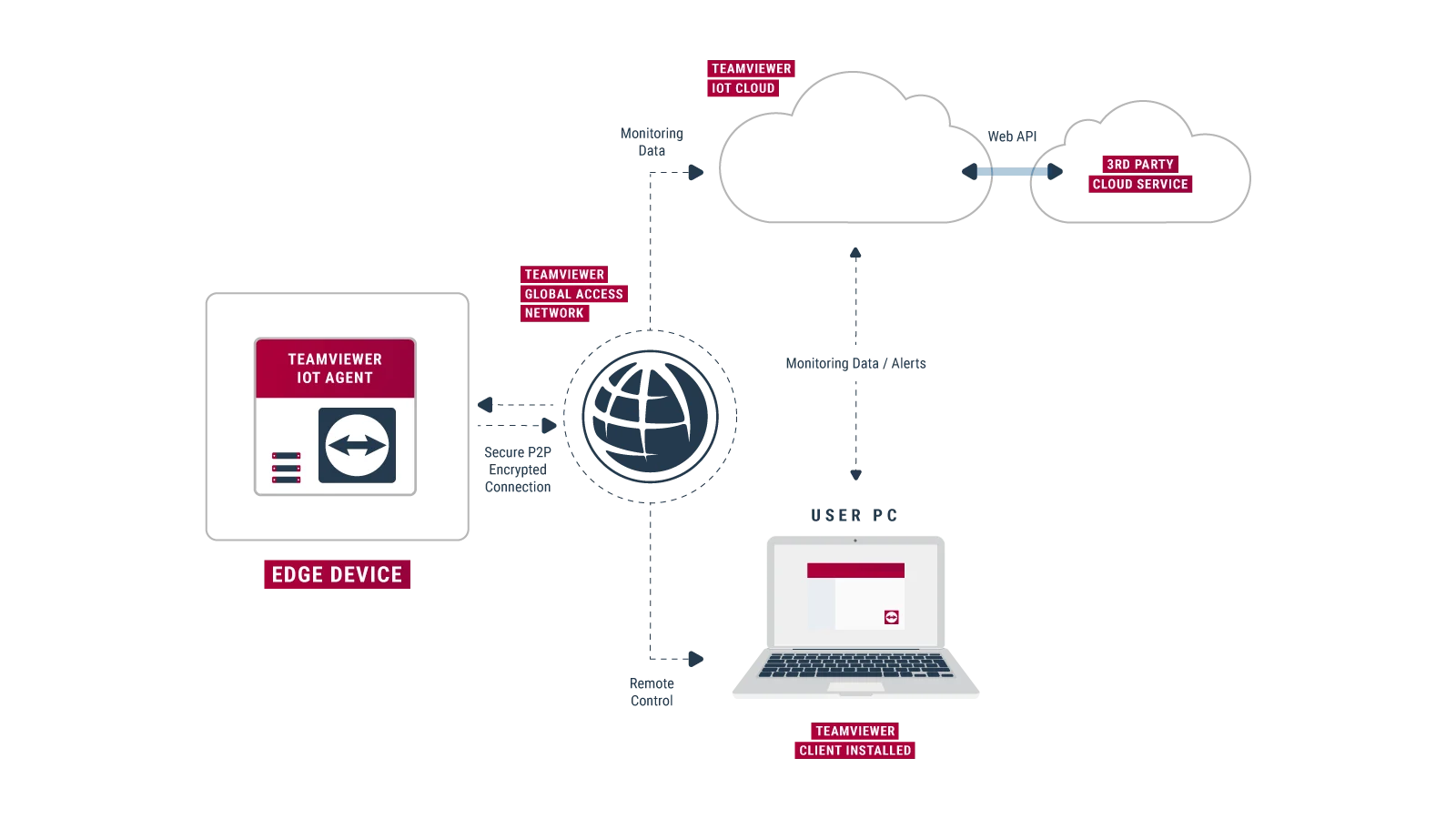
A common method to overcome these obstacles involves using secure VPN tunnels. Services such as SocketXP provide cloud-based IoT device management and remote access platforms that provide SSH access to your IoT devices like Raspberry Pi, Arduino, or any Linux-based embedded systems that are behind NAT routers or firewalls over the internet by using secure SSL/TLS VPN tunnels. This approach creates an encrypted channel, allowing you to bypass firewall restrictions and establish a secure connection.
Within this context, the significance of security cannot be overstated. All network traffic should employ robust encryption protocols such as TLS or DTLS to ensure the confidentiality and integrity of data. Firewalls must be meticulously configured to permit only the essential traffic, thus minimizing the attack surface. Employing VPN connections for remote access further fortifies the security posture of your IoT network.
Imagine a scenario where you want to remotely manage a Raspberry Pi. You can use tools like SocketXP to directly connect to the Raspberry Pi from anywhere, acting as though you were on the local network. No need to hunt for the device's IP address or fiddle with firewall settings. You can send commands, run batch jobs, and access the Pi's desktop through a web portal, streamlining your management tasks.
The process of setting up remote access typically involves several key steps. First, you'll need to select an appropriate remote access solution, such as SocketXP, or an open source alternative. Next, you'll install the necessary software or configure the service on your IoT device. Subsequently, you'll configure your router and firewall to allow the traffic required for remote access, which could include opening specific ports or configuring port forwarding. Finally, you'll establish a secure connection using encryption, and youll be ready to manage your devices remotely.
Remote access for IoT devices behind a router on Android offers a range of possibilities. You can access your home automation system, monitor environmental sensors, or manage industrial equipment from the convenience of your smartphone. For example, you can remotely access your Raspberry Pi, set up a VNC server on the Pi, and use a VNC client on your Android device to view and interact with the Pi's desktop.
Another example is accessing an Arduino, which, when connected to a network, can be remotely controlled through various methods like an SSH tunnel. This allows for programming, data monitoring, and control commands over the internet, provided that the network is set up correctly and securely.
In the industrial sector, remote access is particularly valuable. Technicians can troubleshoot equipment without physically visiting the site, reducing downtime and expenses. Furthermore, businesses can gain valuable insights by monitoring the data generated by these devices, allowing for better decision-making and operational efficiency. A remote access example is the control of machines or monitoring sensors in a remote location, this would otherwise require a costly visit. Remote access provides a continuous stream of data and instant control, thereby streamlining the operation.
The benefits extend beyond convenience. Remote access enables enhanced security. By using secure VPN connections and robust encryption, organizations can protect their IoT devices from unauthorized access and cyberattacks. Furthermore, remote access can improve efficiency by allowing technicians to diagnose and fix problems remotely, reducing the need for expensive on-site visits. Also, remote monitoring enables organizations to optimize their devices and processes, leading to improved performance and cost savings.
However, achieving secure and efficient remote access requires a strategic approach. You must implement a layered security model, incorporating firewalls, encryption, and access controls. Its also important to choose solutions from reputable providers, carefully configure your network, and regularly monitor for potential vulnerabilities. You should be using a VPN connection when you are accessing your IOT network.
Moreover, with the rapid growth of IoT devices, understanding how remote access works behind the scenes is crucial for leveraging the full potential of IoT ecosystems. This includes ensuring secure communication channels, managing device configurations, and monitoring the health and performance of your devices.
The evolution of IoT is closely tied to the necessity for robust remote access solutions. As devices become more interconnected, the need for secure and reliable access has never been more critical. The ability to control and monitor IoT devices remotely is not just a convenience it's a necessity.
Understanding the basics of IoT remote access is crucial for anyone looking to implement IoT remote access behind a firewall. This is due to the increase in smart devices, so being able to manage those devices is essential. Whether it's for personal projects or professional applications, the ability to control and monitor IoT devices remotely is an essential skill in today's digital landscape.
In conclusion, remote access to IoT devices is a critical skill. Whether you're a tech enthusiast, a professional, or a business owner, mastering the art of remote IoT access equips you with the ability to manage, monitor, and troubleshoot your smart devices from anywhere in the world.
The key to successful remote access is to approach it with a combination of technical understanding and a focus on security. By following the guidelines and best practices outlined in this article, you can configure and manage your IoT network effectively, enhancing convenience, efficiency, and, most importantly, security.
By implementing these measures, you can create a secure and efficient remote access environment for your IoT devices, unlocking their full potential and driving innovation in various industries and applications.

Detail Author:
- Name : Claude Anderson
- Username : eldon73
- Email : jwalsh@lockman.com
- Birthdate : 2003-07-17
- Address : 534 Medhurst Mountain Reymundochester, TN 38280-1381
- Phone : 1-352-306-0211
- Company : Jacobi, Lueilwitz and Hand
- Job : Board Of Directors
- Bio : Repudiandae qui enim eaque repellat nihil qui quia. Cupiditate pariatur assumenda est iste ipsum et. Nam deserunt sed architecto voluptas quam atque.
Socials
tiktok:
- url : https://tiktok.com/@muellern
- username : muellern
- bio : Velit mollitia rerum tenetur placeat.
- followers : 5133
- following : 2373
linkedin:
- url : https://linkedin.com/in/neva3097
- username : neva3097
- bio : Sint nemo non id voluptatem ut qui suscipit.
- followers : 270
- following : 951