Access Your IoT Devices Remotely: Behind Router Solutions & Tips
Are you ready to untangle the complexities of remote access to your Internet of Things (IoT) devices? The ability to control your devices from anywhere in the world, irrespective of firewalls and Network Address Translation (NAT) routers, is now a practical reality.
As the digital world evolves, so too does the necessity for seamless connectivity. The Internet of Things (IoT) is no longer a futuristic concept; it's a tangible part of our daily lives. From smart home appliances to industrial sensors, the proliferation of connected devices demands a robust and secure method of remote access. This article delves into the nuances of remote connect IoT behind router, providing expert insights and practical solutions for both beginners and seasoned tech enthusiasts.
Before going further, a note of caution is paramount: security. Always employ strong, unique passwords for all components in your setup: your IoT devices, your router, your VPN (if applicable), and any cloud platform you utilize. Regularly update the firmware on your IoT devices and your router to patch vulnerabilities and maintain optimal performance. This proactive approach is the first line of defense against potential security breaches.
- Elena Moussa Height Weight Body Stats What You Need To Know
- Discover Hdhub4u Latest Movie Updates Free Downloads
Let's begin by dissecting the core challenge: accessing devices that sit behind a NAT router and firewall. A NAT router, the ubiquitous gateway in most home and business networks, translates private IP addresses (used within your network) to a single public IP address (used to communicate with the internet). This inherent design creates a barrier. Furthermore, firewalls, either built-in or separate devices, act as gatekeepers, meticulously controlling incoming and outgoing network traffic.
However, this seemingly insurmountable barrier is surmountable. The strategies employed to overcome these obstacles revolve around several key techniques: port forwarding, Virtual Private Networks (VPNs), and secure tunneling.
One of the most common methods to remotely access devices is port forwarding. This involves configuring your router to "forward" specific incoming traffic on a particular port to a specific device on your internal network. For example, if you want to access a web server running on a Raspberry Pi (connected via Ethernet) on your local network, you would configure port forwarding in your router's settings. This configuration tells the router to send all traffic received on, say, port 80 (the standard HTTP port) to the Raspberry Pi's local IP address. The specific steps for port forwarding vary based on the router model, but the general principle remains consistent. Remember to consult your router's documentation for detailed instructions. Another crucial factor to consider is the use of a static IP address for your IoT device; this prevents the IP address from changing, which would break your port forwarding configuration.
- Sky Cinema More Movies 4k Streaming Tips You Need Now
- Alternatives To Hdmovie2 Stream Movies Find The Best Sites Now
Another approach is establishing a VPN. A VPN creates an encrypted tunnel between your device and your local network. From a remote location, you connect to your VPN server (which could be your router itself, if it supports VPN functionality, or a dedicated VPN server). Once connected, you essentially become part of your local network. Your remote device is assigned an IP address on your local subnet, allowing you to access other devices as if you were physically present. Several VPN protocols are available (OpenVPN, WireGuard, etc.), each with its own strengths and weaknesses; selecting the best option depends on your specific requirements and the capabilities of your router.
The Raspberry Pi, a compact and affordable single-board computer, emerges as an ideal candidate for many IoT remote access implementations. Its versatility, low power consumption, and the extensive support it receives from a vibrant community contribute to its popularity. Whether you need a small server, a network bridge, or a versatile gateway, a Raspberry Pi, configured appropriately, can often fulfill the role. For instance, you can easily host a web page on a Raspberry Pi and access it remotely using port forwarding.
In some instances, especially if you are connecting to devices that lack a sophisticated operating system or user interface, you might consider using SSH (Secure Shell). SSH provides a secure, encrypted connection to a device over the network. This lets you run commands, transfer files, and manage the device remotely. Although using SSH to connect to IoT devices behind a router without Windows may seem complicated, in fact, it can be quite straightforward. The process usually consists of enabling SSH on the IoT device, opening the appropriate port on the router (port forwarding), and then using an SSH client on your remote device to connect. Tools like PuTTY or OpenSSH (available on most operating systems, including macOS and Linux) can be used to establish SSH connections. Remember, as mentioned before, always secure your SSH connections with strong passwords or SSH keys.
Furthermore, if you want to manage your IoT devices remotely using Android devices, the task is now incredibly accessible. There are numerous free Android apps available that simplify the process. These apps typically handle the complexities of establishing and maintaining the remote connection, letting you focus on what is important: accessing and managing your devices. A simple search on the Google Play Store for "SSH client" or "remote access" should yield several valuable results. The key to success lies in properly configuring your router and understanding the basics of networking.
A slightly more advanced method involves using reverse SSH tunnels or a platform like SocketXP. In essence, reverse SSH tunnels allow a device within your local network to initiate an SSH connection to a server on the public internet. This, in turn, allows you to connect to the local device through the server. This method is highly secure and useful in scenarios where you are behind a strict firewall that blocks incoming connections. SocketXP and similar platforms take this approach further by offering features such as automated tunnel management, security, and the ability to selectively expose applications. These can be especially useful for managing devices behind multiple layers of NAT and firewalls.
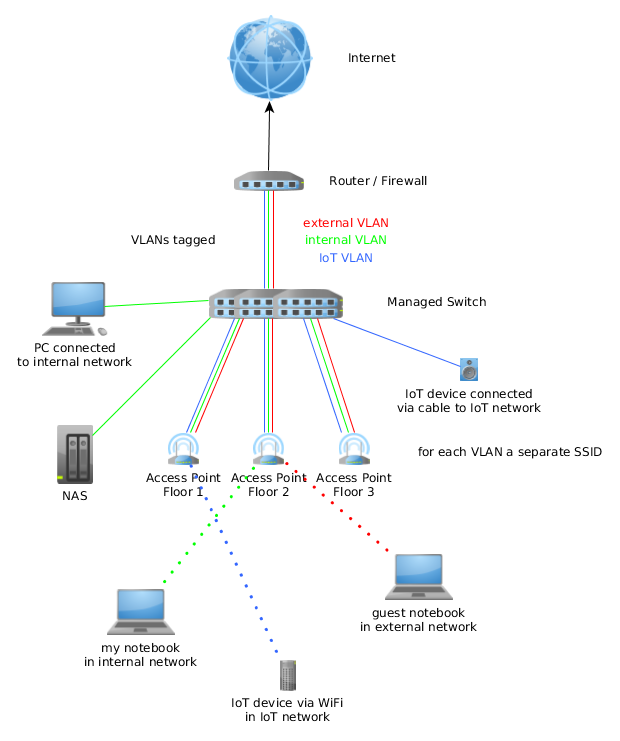
In scenarios where you have multiple routers (for instance, a modem/router provided by your Internet Service Provider (ISP) connected to a secondary router of your own), a technique known as cascading routers is implemented. In this configuration, the inner router sits behind the outer router. To make the inner router accessible, you configure the outer router to forward traffic on a specific port to the inner router's WAN IP address. Then, you configure the inner router itself to forward traffic on the relevant port to your IoT device. This adds an extra layer of complexity, so proper configuration is crucial.
Moreover, the ability to change the band and security settings used by these devices adds an additional layer of security and control. If your device only supports a 2.4 GHz connection, you might consider disabling the 5 GHz bands, and this helps in securing the configuration and reduces the attack surface. When you set up everything, always test your configuration thoroughly by attempting to connect to your remote IoT devices from a remote location and confirm everything works as expected.
Remember, security is paramount. This encompasses strong passwords, up-to-date firmware, and a thorough understanding of your network configuration. When in doubt, err on the side of caution. Double-check your configurations and consider implementing additional security measures such as two-factor authentication (if your devices or services support it).
Ultimately, remote access to IoT devices is no longer a complex endeavor exclusive to experts. By understanding the fundamental concepts, selecting the right tools, and meticulously configuring your network, you can achieve seamless connectivity. Now, with these tools in your arsenal, you can control your connected devices from anywhere in the world, taking advantage of the growing capabilities of the Internet of Things.
| Topic | Details |
|---|---|
| Goal | Providing secure, reliable remote access to Internet of Things (IoT) devices, regardless of network configurations and limitations. |
| Key Challenge | Overcoming barriers such as NAT routers and firewalls that restrict remote access. |
| Solutions |
|
| Essential Tools |
|
| Security Best Practices |
|
| Application Scenarios |
|
| Additional Steps |
|

Detail Author:
- Name : Keely Ullrich
- Username : brent.bechtelar
- Email : maximus.powlowski@padberg.com
- Birthdate : 1992-05-22
- Address : 531 Gutmann Dam Apt. 803 East Titusfurt, FL 05034-1948
- Phone : 1-260-998-6688
- Company : Murphy-Kuhic
- Job : Forensic Investigator
- Bio : Et eum eos minus impedit sit. In eum ad dolores. Iste impedit quia culpa quia.
Socials
twitter:
- url : https://twitter.com/hettiebogan
- username : hettiebogan
- bio : Quod laborum libero vitae reprehenderit molestias sint dolore sint. Sed consequatur omnis vitae nesciunt aut quo. Nam fuga autem dolores ut.
- followers : 6800
- following : 2212
linkedin:
- url : https://linkedin.com/in/hettie.bogan
- username : hettie.bogan
- bio : Quae enim temporibus voluptatibus beatae quae.
- followers : 4767
- following : 754
facebook:
- url : https://facebook.com/hettie818
- username : hettie818
- bio : Et et similique nulla. Quia ut vel distinctio excepturi facilis natus aliquid.
- followers : 255
- following : 2510
tiktok:
- url : https://tiktok.com/@hettiebogan
- username : hettiebogan
- bio : Cum repellendus labore dolorem in.
- followers : 4487
- following : 1165
instagram:
- url : https://instagram.com/hettiebogan
- username : hettiebogan
- bio : Sed temporibus est officiis voluptates excepturi. Sed non quam et.
- followers : 6485
- following : 418