Secure Your IoT: Remote Platform SSH Keys For Raspberry Pi
Are you wrestling with the security of your Internet of Things (IoT) devices, particularly your Raspberry Pis? The proliferation of interconnected devices has created a landscape where securing access is not just a best practice, but an absolute necessity.
In a world increasingly reliant on remote monitoring and control, the ability to securely access and manage your IoT devices from anywhere is paramount. This guide delves deep into the world of secure access to your Raspberry Pi devices, focusing on the use of Secure Shell (SSH) keys and the platforms that simplify their management. Whether you're a seasoned developer or just starting your IoT journey, the information provided within these pages will empower you to fortify your setup and safeguard your valuable data.
At the heart of secure remote access lies SSH, a cryptographic network protocol that provides a secure channel over an unsecured network. This is where SSH keys come into play. SSH keys are cryptographic keys used to authenticate users when connecting to remote servers or devices. They provide a more secure and convenient alternative to password-based authentication. Unlike passwords, SSH keys are much harder to crack, significantly reducing the risk of unauthorized access to your devices. In addition, SSH keys are generated in pairs: a public key and a private key. The public key is placed on the remote device, while the private key is kept securely on the user's computer. When a connection is initiated, the remote device uses the public key to verify the user's identity, and the user's private key decrypts the challenge, allowing access.
- Vegamovies In 2024 Risks Trends Alternatives Latest News
- Hdhub4u Free Movies Safety Concerns Alternatives 2024 Guide
Let's imagine a world where your home automation system, powered by a Raspberry Pi, is accessible from anywhere. You can control lights, monitor security cameras, and adjust your thermostat, all remotely. But what if someone gained unauthorized access to this system? The potential consequences are unsettling: data breaches, manipulation of your devices, and compromise of your personal information. Securing your Raspberry Pi is not just about convenience; it's about safeguarding your privacy, your data, and your peace of mind.
Many of the remote monitoring and alerting platforms often provide the ability to execute commands on the Raspberry Pi. They can also provide the ability to view device status, such as CPU usage, memory usage, and disk space. The best platforms will also offer customized alerts that can be sent via email, SMS, or other methods.
The challenge of securing remote access becomes even more complex when dealing with multiple devices. Manually managing SSH keys for each individual device can be a time-consuming and error-prone process. It is a process that can easily expose you to security vulnerabilities if not properly implemented. The solution lies in leveraging remote IoT platforms that offer robust SSH key management features.
- Free Movie Streaming Guide Your Guide To Free Movies More
- Best Vegamoviesmen Alternatives Free Movie Sites 2024
These platforms streamline the process of generating, distributing, and managing SSH keys for all your Raspberry Pi devices. They eliminate the need for manual key management, reduce the risk of human error, and provide a centralized interface for controlling access to your devices. These platforms offer a more secure and convenient way to manage SSH keys, enabling users to efficiently secure multiple devices.
But what makes a good remote IoT platform for SSH key management? One of the key features is the ability to generate and manage SSH keys. The platform should allow you to easily generate key pairs, distribute public keys to your devices, and store private keys securely. Ideally, the platform also provides a way to revoke access if needed, for example, if a device is lost or compromised.
Another critical aspect is security. The platform should implement robust security measures to protect your SSH keys from unauthorized access. This includes using encryption to protect key storage and implementing access controls to restrict who can manage keys. In addition, the platform should provide audit logs that track all key management activities, providing transparency and accountability.
Now, let's consider some of the leading platforms for SSH key management. Several platforms stand out for their focus on security and ease of use. These platforms offer a range of features, including key generation, distribution, and management, as well as robust security measures to protect your SSH keys from unauthorized access. These platforms, provide a streamlined solution for businesses and individuals, eliminating the complexities of manual key management. These provide a secure environment for both the public and private keys.
Many of these platforms offer cloud-based solutions which provide users with the ability to access their devices from anywhere in the world. Other platforms offer on-premise solutions for enhanced security and control.
When choosing a remote IoT platform, it's important to consider several factors. Firstly, evaluate the platform's security features. Ensure that it uses strong encryption for key storage and transport and that it implements access controls to restrict who can manage keys. Check for audit logs to track all key management activities. Secondly, assess the platform's ease of use. The platform should be easy to set up and configure, with a user-friendly interface. It should also provide clear documentation and helpful support resources.
Moreover, consider the platform's compatibility with your devices. Make sure the platform supports the Raspberry Pi and any other devices you plan to use. Finally, consider the platform's cost. Evaluate the pricing plans and choose the one that best suits your budget and needs. Some platforms offer free tiers with limited functionality, while others offer paid plans with more advanced features and higher levels of support.
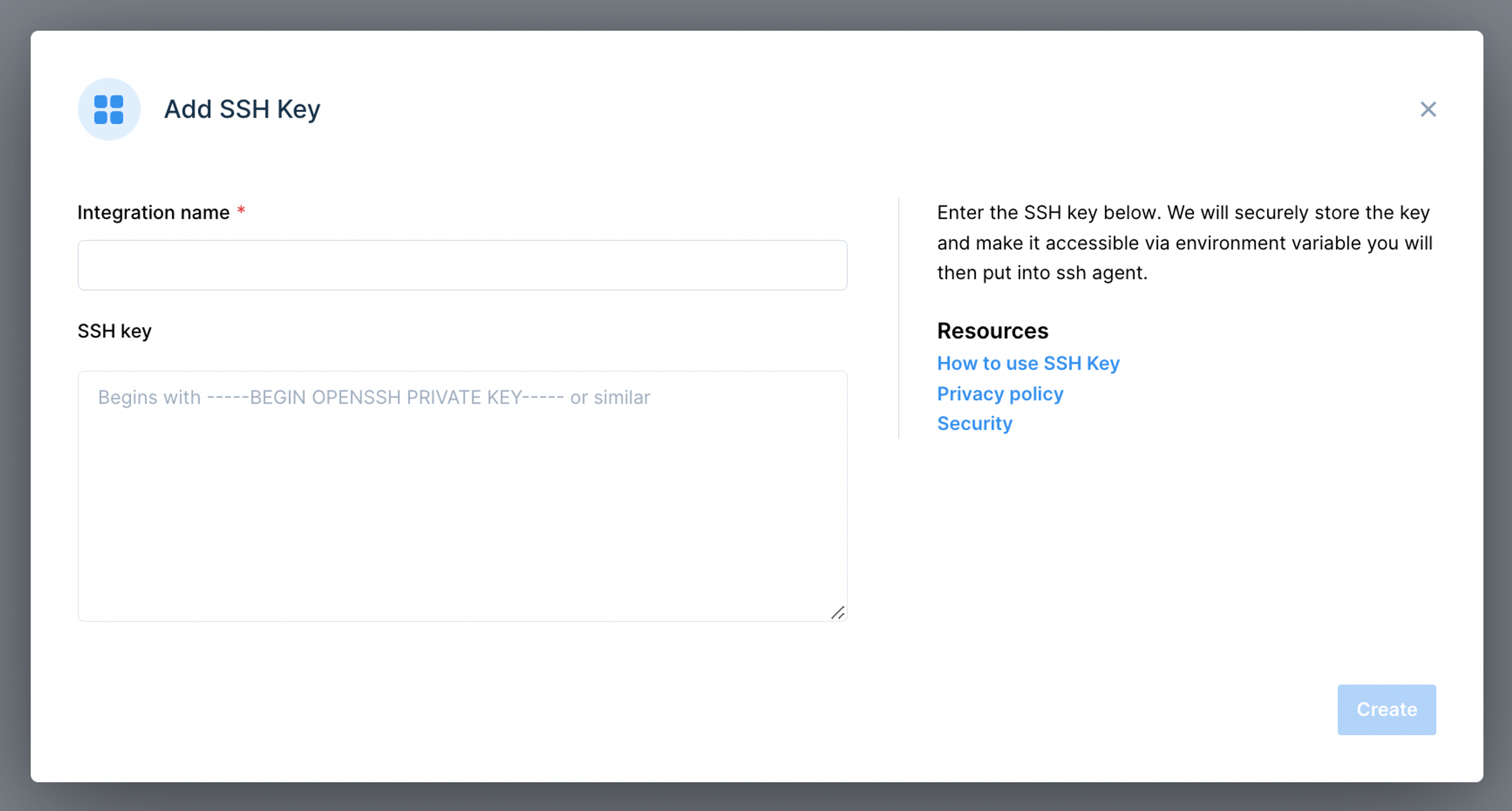
Once you've chosen your remote IoT platform, the next step is to set up SSH keys. The platform will typically guide you through the process of generating a key pair. You will then need to upload the public key to your Raspberry Pi and store the private key securely on the device or system you use to connect to your Raspberry Pi.
The process of setting up SSH keys typically involves several steps. First, generate an SSH key pair on your local machine using the `ssh-keygen` command. When prompted, choose a strong passphrase to protect your private key. Then, copy the public key to your Raspberry Pi by either using the `ssh-copy-id` command or manually appending the public key to the `~/.ssh/authorized_keys` file on the Pi. Finally, disable password authentication on your Raspberry Pi by editing the `/etc/ssh/sshd_config` file and setting `PasswordAuthentication` to `no`.
With SSH keys configured, you can now connect to your Raspberry Pi without using a password. This significantly enhances the security of your connection. You can further improve your setup by changing the default SSH port. This helps to deter automated attacks that often target the default port 22. Consider using firewall rules to restrict SSH access to specific IP addresses or networks, further reducing the attack surface of your Raspberry Pi.
By securing your SSH setup, you create a secure foundation for your IoT projects. This gives you the freedom to experiment, innovate, and build without sacrificing the security of your devices and data. It ensures your device will be available and accessible only to the authorized users.
The use of a remote IoT platform will drastically improve the security of your remote devices by streamlining key management and securing the connection protocols used to communicate with your Raspberry Pis. Using this will give you peace of mind knowing that your devices are protected from unauthorized access and that your data is safe.
In the ever-evolving landscape of IoT, where devices are constantly connected, the best way to protect yourself is by using SSH keys. It is no longer a complex task; it is a necessity. By doing so, you can confidently embrace the potential of IoT, creating innovative solutions without compromising the security of your devices.
Let's get you started with some of the essential considerations.
Here's a table that offers a comparative analysis to help guide your decision-making process.
The following table includes the general information and the benefits of remote access to IoT devices
| Aspect | Details |
|---|---|
| Definition of IoT Remote Access | The capability to remotely monitor, manage, and control Internet of Things (IoT) devices from a distance. This includes the ability to access device data, configure settings, and execute commands. |
| Key Benefits |
|
| Security Measures |
|
| Example Applications |
|
| Platform Considerations |
|
Disclaimer: The information provided here is for informational purposes only and does not constitute professional advice. Security practices and technologies are constantly evolving, and users are encouraged to stay updated on the latest developments.
Managing remote devices securely is a growing challenge in today's interconnected world, and remoteIoT platform SSH key free offers a robust solution for businesses and individuals alike, providing a secure mechanism for encrypting and encapsulating private network traffic and moving it through an intermediate network. For more information and further reading on related topics, please visit zenodo.org.

Detail Author:
- Name : Dr. Max Bins
- Username : waelchi.thea
- Email : max.willms@hotmail.com
- Birthdate : 2007-01-17
- Address : 601 Casey Divide Port Vernie, GA 43195
- Phone : 1-732-886-7108
- Company : Stoltenberg-Oberbrunner
- Job : Buyer
- Bio : Sunt quisquam voluptatem ducimus ipsam a rerum. Occaecati voluptatem expedita aspernatur reprehenderit quia illo vel. Aut aut fugiat enim.
Socials
twitter:
- url : https://twitter.com/tremblayp
- username : tremblayp
- bio : Qui optio debitis magnam ea. Incidunt modi aliquid vel consequatur. Quam unde animi sed.
- followers : 4414
- following : 960
instagram:
- url : https://instagram.com/tremblayp
- username : tremblayp
- bio : Eos et minima fugit non. Eum aut qui vel neque aut sint. Et illum eos magnam a.
- followers : 1135
- following : 2959
linkedin:
- url : https://linkedin.com/in/pablotremblay
- username : pablotremblay
- bio : Accusamus facere enim voluptas quis.
- followers : 756
- following : 1865