Remote IoT Web SSH: Secure Access & Management Guide
Are you tired of juggling multiple tools and battling security concerns when managing your Internet of Things (IoT) devices remotely? The ability to securely access and control your IoT devices from anywhere in the world is no longer a luxury; it's a necessity, and the right remote IoT Web SSH solution is the key to unlocking this potential.
The rise of the Internet of Things has ushered in an era of unprecedented connectivity, with devices ranging from smart home appliances to industrial sensors becoming integral parts of our daily lives and business operations. This proliferation of connected devices, however, presents a unique set of challenges, particularly when it comes to remote management and security. Traditional methods of accessing and controlling these devices, often relying on insecure protocols or complex VPN configurations, are no longer sufficient in today's threat landscape.
Consider the scenario: You're overseeing a critical IoT project, perhaps a network of sensors monitoring environmental conditions in a remote location, or maybe a fleet of industrial robots operating on a factory floor. The ability to monitor these devices, diagnose issues, and implement updates remotely is paramount. Yet, the prospect of traveling to each physical location every time a problem arises is impractical and costly. Moreover, the need to ensure the security of these devices and the sensitive data they collect is of the utmost importance.
- Amy Carter Today Life After The White House Jimmy Carters Legacy
- Find Movies Stream In India Justwatch Vegamovies More
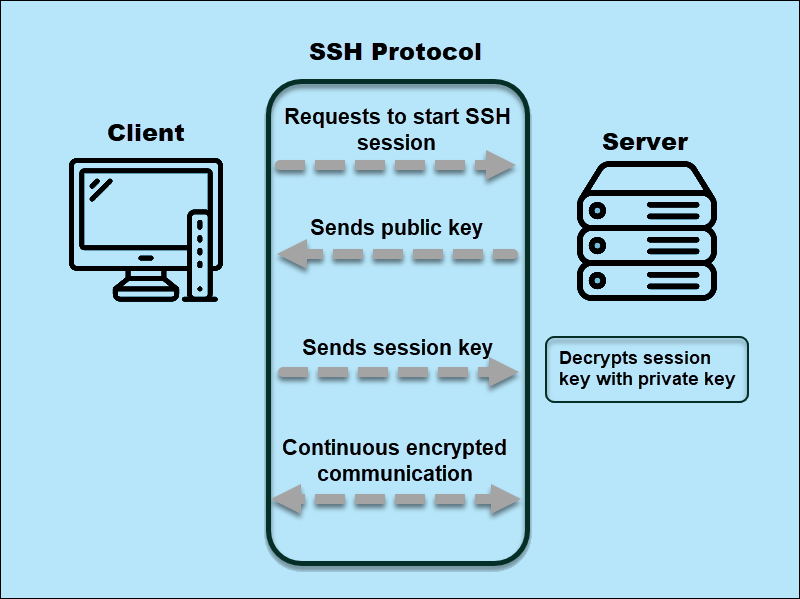
This is where the power of Remote IoT Web SSH solutions comes into play. By leveraging the robust security of Secure Shell (SSH) protocols and the accessibility of web browsers, these tools provide a seamless and secure bridge between you and your remote IoT devices, allowing you to manage them from virtually any location.
For Windows users managing IoT devices, tools like MobaXterm offer a convenient and feature-rich solution. MobaXterm provides a tabbed interface, allowing you to manage multiple SSH connections simultaneously, along with a built-in X server for graphical application forwarding. For teams requiring easy and secure access, Tailscale SSH provides a simplified and secure way to connect devices, creating a private network that bypasses the complexities of traditional VPN setups.
The core principle behind Remote IoT Web SSH is simple: it establishes a secure, encrypted tunnel between your device and the remote IoT device or server. This tunnel protects your data from eavesdropping and unauthorized access, ensuring that all communication remains confidential. Authentication mechanisms, such as password-based or key-based authentication, further enhance security, verifying the identity of the user before granting access. Furthermore, the implementation of SSH allows for features like port forwarding, which enables you to access services running on the remote device through the secure tunnel. This means you can connect to databases, web servers, and other applications as if they were running locally.
- Unanswered Amy Carters Husband No Results Find Out
- Andrew Garfields Relationships Dating Breakups More
The beauty of Remote IoT Web SSH solutions lies in their versatility and adaptability. They can be used to manage a wide range of IoT devices, from single-board computers like the Raspberry Pi to industrial control systems. Their ability to provide secure remote access to servers and devices is invaluable in various fields, including:
- Industrial Automation: Remotely manage and monitor industrial control systems, robots, and other automated equipment.
- Smart Agriculture: Monitor and control irrigation systems, environmental sensors, and other agricultural devices from any location.
- Home Automation: Access and control smart home devices, such as lighting systems, thermostats, and security cameras, from your web browser.
- Research and Development: Remotely access and control laboratory equipment, data acquisition systems, and other scientific instruments.
- IT Support: Provide remote support and maintenance for IoT devices deployed in the field.
The benefits of utilizing Remote IoT Web SSH solutions extend beyond security and convenience. By enabling remote access and management, these tools contribute to increased efficiency and reduced operational costs. Here's a breakdown of key advantages:
- Enhanced Security: The use of SSH encryption protects data in transit, mitigating the risk of data breaches and unauthorized access.
- Improved Efficiency: Remote access eliminates the need for on-site visits, saving time and resources.
- Reduced Costs: Minimizing travel and maintenance costs translates to significant savings.
- Increased Productivity: Effortlessly manage devices from any location, increasing productivity.
- Centralized Management: Remote tools enable the management of a large number of devices from a central location.
Here's a table of best practices to make your work easier and to keep your data secured while working on remote IoT devices through the web.
| Area | Best Practices | Explanation |
|---|---|---|
| Configuration of SSH | Strong Passwords | Always generate and use strong, unique passwords for your SSH accounts. Avoid easily guessable passwords. |
| Key-Based Authentication | Implement SSH key-based authentication. This is significantly more secure than password-based authentication. Disable password login if possible. | |
| Disable Root Login | Disable direct root login via SSH. Create a regular user account with sudo privileges and use that to log in. | |
| Port Customization | Change the default SSH port (22) to a non-standard port. This makes it more difficult for automated attacks. | |
| Firewall Rules | Configure your firewall to allow SSH traffic only from trusted IP addresses or networks. | |
| Securing Your Setup | Regular Updates | Keep your SSH server and client software up-to-date with the latest security patches. |
| Two-Factor Authentication (2FA) | Enable two-factor authentication for an extra layer of security. | |
| Monitoring and Logging | Enable SSH logging to monitor for suspicious activity, such as failed login attempts. Use security information and event management (SIEM) tools to collect and analyze logs. | |
| Regular Audits | Conduct regular security audits and vulnerability scans to identify and address potential weaknesses. | |
| Optimizing Performance | Optimize SSH Configuration | Adjust SSH settings such as connection timeouts and keep-alive intervals to optimize performance based on your network conditions. |
| Bandwidth Considerations | Consider the bandwidth limitations of your network connection. Use compression (e.g., gzip) if appropriate. | |
| Resource Monitoring | Monitor the resource usage of the remote device (CPU, memory, disk I/O) to ensure optimal performance. | |
| Choose the Right Tools | Select Remote IoT Web SSH tools that meets all your requirements for better experience. |
The integration of Remote IoT Web SSH into your IoT management strategy will greatly enhance your security and operational efficiency. However, it is vital to select the right tools and implement the best practices. Here's a review of some of the solutions and tools on the market:
- MobaXterm: A popular choice for Windows users, MobaXterm provides a comprehensive solution with a built-in SSH client, an X server, and a tabbed interface for managing multiple connections.
- Tailscale SSH: Tailscale offers a secure and straightforward approach to establishing a private network for remote access. It simplifies SSH access and is especially effective for teams.
- Web-Based SSH Clients: Various web-based SSH clients allow access from a standard web browser, offering accessibility from any device with an internet connection.
Let's delve into setting up a secure Remote IoT Web SSH connection for a Raspberry Pi. This is a common scenario, as Raspberry Pis are widely used in various IoT applications. This guide covers the fundamental steps:
- Enable SSH on your Raspberry Pi: The first step is to ensure that SSH is enabled on your Raspberry Pi. Connect a monitor, keyboard, and mouse, then use the Raspberry Pi configuration tool (raspi-config) to enable SSH. Alternatively, you can create an empty file named "ssh" (without any file extension) in the boot partition of your SD card before first boot.
- Configure the Raspberry Pi's IP Address: You'll need to know your Raspberry Pi's IP address to connect to it remotely. You can find this through your router's interface or by using the `ifconfig` command on the Raspberry Pi itself. Consider setting a static IP address or using DHCP reservation in your router to prevent the IP address from changing.
- Configure SSH Key-Based Authentication (Recommended): This is the most secure way to connect. Generate an SSH key pair on your local machine (the one you'll use to connect). Copy the public key to the authorized_keys file on your Raspberry Pi.
- Test the SSH Connection: Using your SSH client, attempt to connect to your Raspberry Pi using its IP address and the username you set up. For example: `ssh pi@`.
- Implement Additional Security Measures: Change the default SSH port (22), disable root login, and configure your firewall, as mentioned above.
- Utilize a Web-Based SSH Client (If Desired): If you want to access your Raspberry Pi from a web browser, you can set up a web-based SSH client. Some options include:
- Shell in a Box: A lightweight web server that presents an SSH session in your browser.
- Apache Guacamole: A more feature-rich solution that supports SSH and other protocols.
The path to a secure and seamless Remote IoT Web SSH experience is within your grasp. By embracing best practices, understanding the tools available, and staying informed on the latest security threats, you can successfully navigate the challenges of managing your IoT devices remotely. Whether you're a seasoned professional or a tech enthusiast, the ability to remotely access and control your devices is essential in today's interconnected world.
Remember that regular updates to the software, strong passwords, and proper security audits are vital. As the technology advances and new vulnerabilities emerge, remaining proactive in protecting your IoT network is essential. You can create a secure, reliable, and scalable system for remotely managing your IoT devices by adhering to these best practices.
The benefits are clear: enhanced security, improved efficiency, and cost savings are achievable through the thoughtful application of remote IoT Web SSH solutions. The world of IoT continues to evolve, and the ability to stay connected to your devices from any location is critical to maintaining operational efficiency and safeguarding data.
The world of remote access is changing rapidly. Make sure you have the tools and knowledge needed to succeed. By implementing secure, scalable, and efficient SSH solutions, you can guarantee safe and reliable remote IoT device management.


Detail Author:
- Name : Jadon Trantow DDS
- Username : koby.graham
- Email : kozey.ezekiel@lockman.net
- Birthdate : 1971-02-25
- Address : 488 Demarcus Stream Port Gilesburgh, VA 42119-7337
- Phone : 1-520-940-1897
- Company : Schimmel, Shanahan and Walter
- Job : Animal Trainer
- Bio : Eum aut numquam sed veritatis vel enim. Facere aliquid sed neque corporis. Laboriosam sed maiores deserunt ab architecto.
Socials
linkedin:
- url : https://linkedin.com/in/rrice
- username : rrice
- bio : Et quis dolore officiis nam quia alias.
- followers : 5429
- following : 1881
facebook:
- url : https://facebook.com/raymond8697
- username : raymond8697
- bio : Corporis et qui quia illo facilis rerum iure. Enim error quidem at aut ipsa.
- followers : 4740
- following : 175
tiktok:
- url : https://tiktok.com/@ricer
- username : ricer
- bio : Deserunt corrupti et consequatur ex quia recusandae id.
- followers : 5223
- following : 1493
instagram:
- url : https://instagram.com/raymond_rice
- username : raymond_rice
- bio : Dolorem ut suscipit sed commodi in dolore omnis sint. Sed sit delectus tenetur voluptas placeat.
- followers : 2876
- following : 238
twitter:
- url : https://twitter.com/rrice
- username : rrice
- bio : Id aperiam et eos ullam excepturi. Et sint sunt modi eum quae a saepe sunt. Architecto saepe natus amet natus non repellat quaerat sunt.
- followers : 4778
- following : 1219