IoT Devices Behind Firewalls & NAT: Remote Access & Control
Is it possible to effortlessly control and manage your Internet of Things (IoT) devices, even when they're tucked behind the protective layers of firewalls and Network Address Translation (NAT) routers? The answer is a resounding yes, and the key lies in understanding and implementing secure remote access techniques.
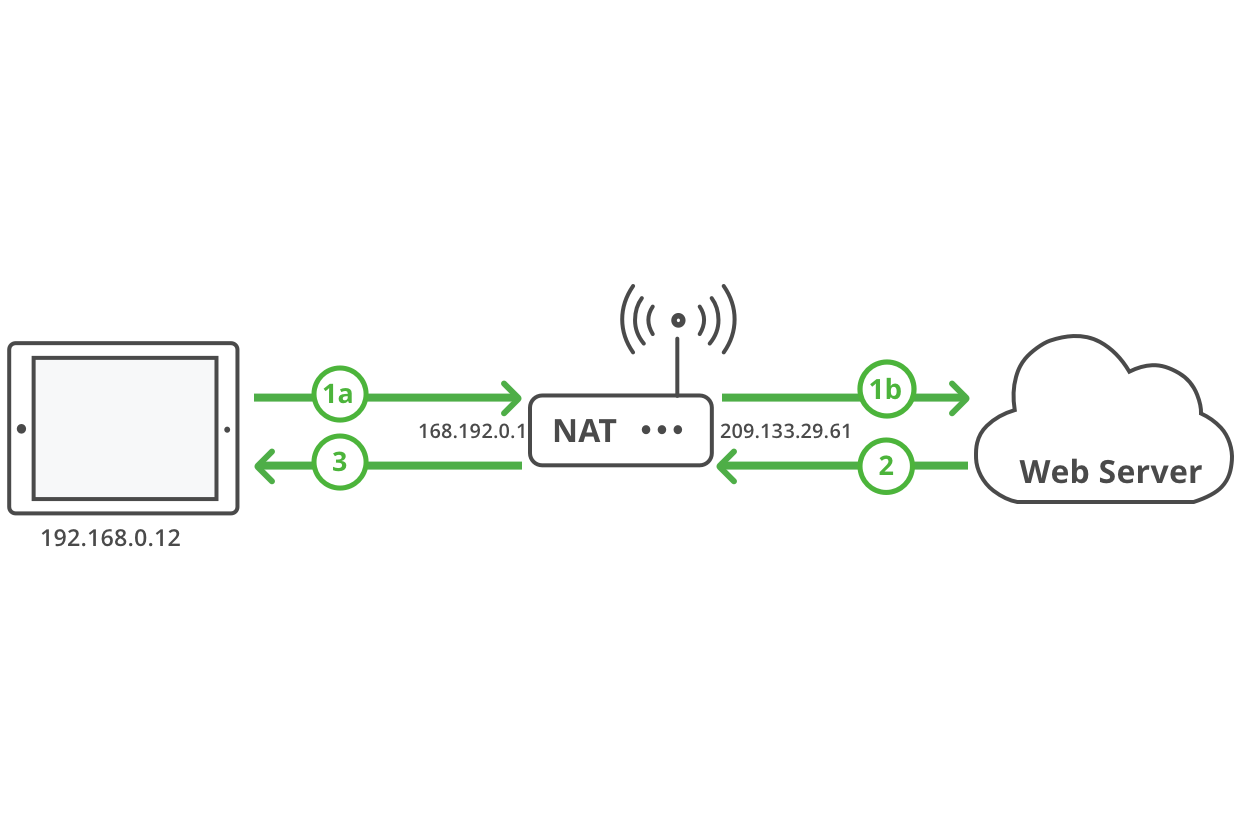
The modern landscape of connected devices presents a unique set of challenges, particularly when it comes to remote management. IoT devices, from smart home gadgets to industrial sensors, are often deployed in environments with restrictive network configurations. These configurations, designed to enhance security, can inadvertently create barriers to remote access, making it difficult to monitor, control, and maintain these crucial components of our increasingly interconnected world. The complexity arises from the fact that these devices often reside behind NAT routers and firewalls, making direct access from the internet a hurdle. To address this, various solutions have emerged, each offering a unique approach to circumventing these obstacles and providing secure remote access to IoT devices.
| Aspect | Details |
|---|---|
| Concept | Remote access and management of Internet of Things (IoT) devices that are behind NAT routers and firewalls. |
| Challenges | Direct access from the internet is blocked, requiring methods to bypass or circumvent these network restrictions. No need to discover the iot device ip and change any firewall settings. |
| Technologies/Methods | Reverse SSH tunneling, utilizing a trusted server to establish a connection, remote access platforms (e.g., SocketXP), and solutions using Raspberry Pi. |
| Benefits | Enables remote monitoring, control, and maintenance of IoT devices from anywhere. Simplifies management and troubleshooting without requiring complex network configurations. |
| Use Cases | Smart home automation, industrial monitoring, remote equipment maintenance, and any scenario where IoT devices need to be accessed remotely. |
| Considerations | Security measures, platform choice, network configuration, and the specific requirements of the IoT device and application. |
| Related Terms | SSH, NAT, firewall, IoT, remote access, Raspberry Pi, command and control, reverse SSH tunnel. |
| Reference Website | Example IoT Remote Access Guide |
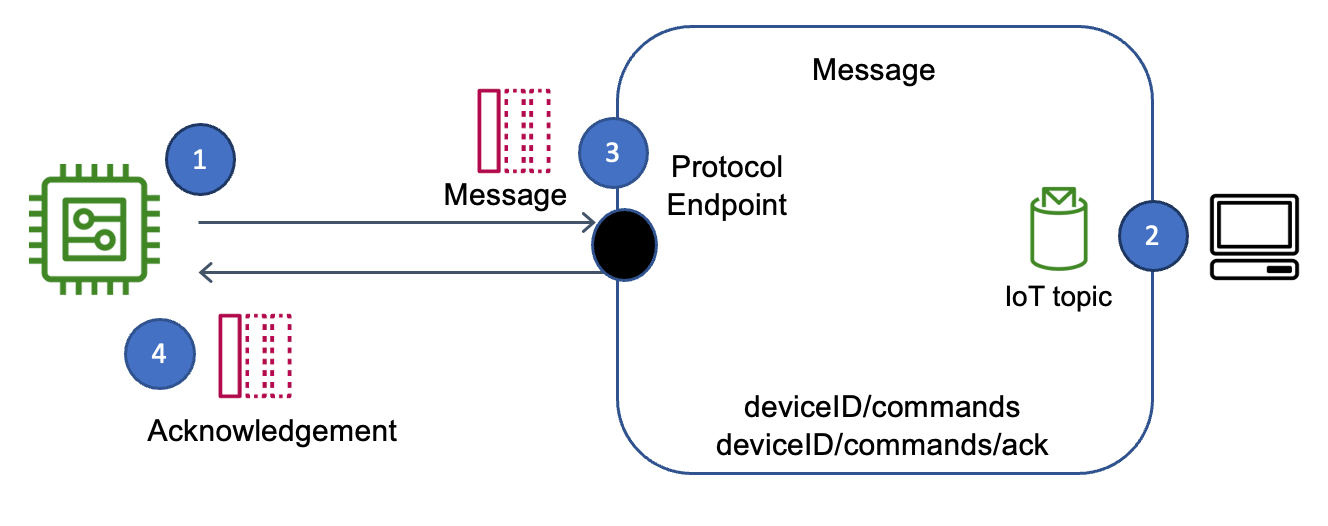
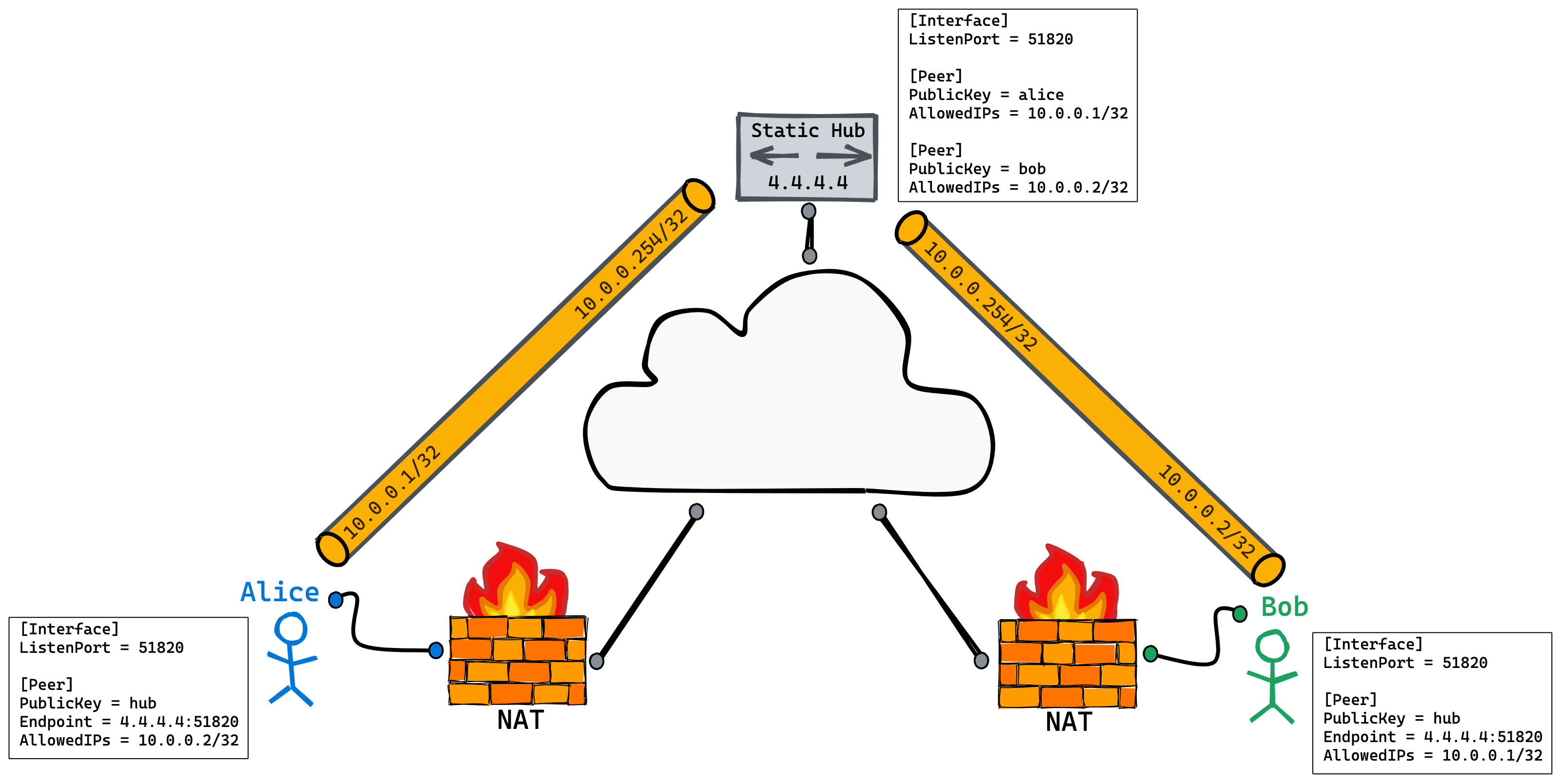
One of the most common and effective approaches involves utilizing the Secure Shell (SSH) protocol. An IoT device can establish an SSH connection to a trusted server, effectively bypassing the need for direct router configuration or public IP addresses. The device initiates this connection, creating a secure tunnel through which commands and data can flow. The server doesn't need to know the device's IP address; the connection is established from the device to a pre-defined endpoint, often a server under your control. This "reverse SSH tunnel" is a cornerstone of secure remote access, allowing for a secure, encrypted channel that traverses firewalls and NAT configurations with relative ease.
- Find Streaming India Movie Tv Guide Vegamovies Alternatives
- Movierulz Everything You Need To Know Legal Alternatives
The architecture often involves a Command and Control (C&C) server that sends requests to the device, which then responds accordingly. This interaction model is frequently observed in IoT applications. The client software, such as a smartphone app or a computer program, sends commands to the smart device acting as a server. These commands can trigger actions like playing or pausing media, starting a process, or retrieving sensor data. This architecture enables bi-directional communication, allowing the remote management of the IoT device.
Tools such as SocketXP provide remote access solutions to address this challenge. With solutions like this in place, an IoT device can connect to a remote server, allowing users to connect to their devices from anywhere. This eliminates the need to discover the device's IP address or change firewall settings, simplifying remote management.
The Raspberry Pi is another powerful tool for remote management. It can act as a gateway, allowing remote access to devices behind firewalls. The process often involves setting up the Raspberry Pi, installing necessary software, and configuring it to forward traffic to the internal devices. This enables secure access to the Raspberry Pi from anywhere, and the device acts as a proxy for other devices on the local network.
- Sung Hoon Ryu Hyun Kyung Split Dating Rumors Honest Revelations
- Drew Starkey The Rise Of Rafe Cameron In Outer Banks Beyond
Several steps are involved in setting up a Raspberry Pi for remote access. One of the primary methods involves using SSH. By using SSH, a user can remotely access the terminal window on another device. Another approach involves creating a web portal that enables sending commands and batch jobs to the Raspberry Pi. Moreover, one can use device trees, which facilitates managing the connected devices through a remote dashboard.
For instance, to remotely access a Raspberry Pi behind a firewall or NAT router, the user can create a reverse SSH tunnel. This involves creating a secure connection to the Raspberry Pi and then using the SSH tunnel to connect to the device. Similarly, port forwarding on the router allows access to the device outside of the local network. Both of these methods contribute to unlocking the full potential of IoT devices securely and efficiently.
Another crucial aspect of remote management is security. Protecting the IoT devices and the network requires multiple layers of security measures. This includes robust authentication, encryption, and regular security audits. A key element is using secure protocols like SSH with strong key-based authentication. Regular updates and monitoring are also essential to prevent security breaches.
Remote access solutions can be integrated with various platforms. These platforms can provide features such as automated maintenance, the ability to monitor device sensor readings and performance, and the option to send commands. This integration helps streamline the management process and provides real-time data, making remote management efficient and user-friendly.
The process of setting up and configuring an IoT device to receive commands remotely involves configuring the device, installing a socketxp agent or similar software, and establishing the necessary network connections. The main task is to create a secure way for the client (user) to communicate with the IoT device, with the device acting as a server. This is frequently accomplished via APIs, which allow the user to send simple commands via the internet.
Understanding the four main communication patterns in IoTtelemetry, inquiry, command, and notificationis essential for the smooth operation of remote management. Telemetry involves sending sensor data from the device to the central server. Inquiry allows the server to request data from the device. Command enables remote control of the device. Notification informs the server or the user of critical events.
In managing IoT devices, overcoming the challenges of reaching a device behind NAT or roaming on mobile networks is crucial. By using reverse SSH tunneling or cloud-based platforms, this issue can be mitigated effectively. In case a user has a problem with remote access, they can easily reset their access, and they can also employ free Android tools for accessing and controlling smart devices remotely.
In essence, enabling remote SSH IoT is all about unlocking the full potential of your devices. The best approach includes secure and efficient ways to manage the devices remotely, ensuring they stay protected while providing all the advantages of connected devices. These methods permit one to directly access the devices behind a firewall from any location and connect to the local network seamlessly.
Remote access to Raspberry Pi devices via the web is another notable implementation. By implementing remote management techniques, one can access the Pi's web interface, control its functions, and retrieve essential data from any location.
In the rapidly evolving world of managing IoT devices, ensuring secure remote access to devices behind firewalls and NAT routers is of utmost importance. Many tools and techniques allow access to devices, like Raspberry Pis, and can be used for free. It involves exploring the tools and techniques to access SSH remote IoT devices, the secure ways to remotely manage Raspberry Pi web devices. The solutions are designed to provide users with the ability to control IoT devices using a web browser.
Detail Author:
- Name : Barbara Kihn DVM
- Username : mathilde16
- Email : zvonrueden@robel.com
- Birthdate : 2007-05-03
- Address : 2116 Weimann Plains Wiegandtown, IN 25271-1200
- Phone : 478-712-2971
- Company : Schuppe, Greenholt and Beatty
- Job : Press Machine Setter, Operator
- Bio : Autem est iusto facilis nisi. Est quia sit et et ex praesentium sapiente. Qui sit eos consequatur id porro numquam. Molestias nobis aut ea esse. Alias non quis nam architecto officiis sint.
Socials
linkedin:
- url : https://linkedin.com/in/ljenkins
- username : ljenkins
- bio : Placeat nihil laboriosam eligendi quam voluptate.
- followers : 5559
- following : 2979
tiktok:
- url : https://tiktok.com/@laurel.jenkins
- username : laurel.jenkins
- bio : Nobis consequuntur iure voluptatem commodi fugiat ipsam corporis.
- followers : 4032
- following : 1610
facebook:
- url : https://facebook.com/laurel_jenkins
- username : laurel_jenkins
- bio : Exercitationem deleniti recusandae iure.
- followers : 1872
- following : 1985
twitter:
- url : https://twitter.com/jenkinsl
- username : jenkinsl
- bio : Consequatur ut sit maxime voluptate impedit hic. Iste at deleniti voluptatibus similique quis. Aut aut atque illo mollitia est ut.
- followers : 818
- following : 1886
instagram:
- url : https://instagram.com/ljenkins
- username : ljenkins
- bio : Suscipit blanditiis odio corrupti vel. Velit odio in cumque qui omnis.
- followers : 2593
- following : 708