IoT Access Anywhere: Solutions & Remote Control Benefits
Can you truly control your world from anywhere? The promise of "IoT access from anywhere" is more than just a futuristic fantasy; it's a tangible reality reshaping how we interact with our homes, offices, and the very fabric of our lives.
The digital age has birthed an era where our devices, the very infrastructure of our daily existence, are becoming increasingly interconnected. This interconnectedness, fuelled by the Internet of Things (IoT), allows for a level of remote control and monitoring previously confined to the realm of science fiction. But what does "IoT access from anywhere" truly mean, and how is it changing our world?
At its core, IoT access from anywhere refers to the ability to connect to and control your IoT devices, regardless of your physical location. This could encompass anything from adjusting your thermostat and arming your security system from across town, to managing industrial machinery on a factory floor from a remote office, or even monitoring a fleet of vehicles from a centralized hub. The possibilities are vast, and the applications span across numerous sectors, from residential to commercial, and even industrial.
- Savannah Bonds Net Worth 2024 Latest Estimates Insights
- Failed Search Results Common Fixes Preventing No Results Errors
This technology is not just a boon for individuals seeking convenience. Its a game-changer for businesses, offering unprecedented opportunities for efficiency, cost savings, and enhanced security. Think about the ability to remotely diagnose and repair equipment, optimize energy consumption, or monitor assets in real-time. These are just a few of the advantages that IoT access from anywhere provides.
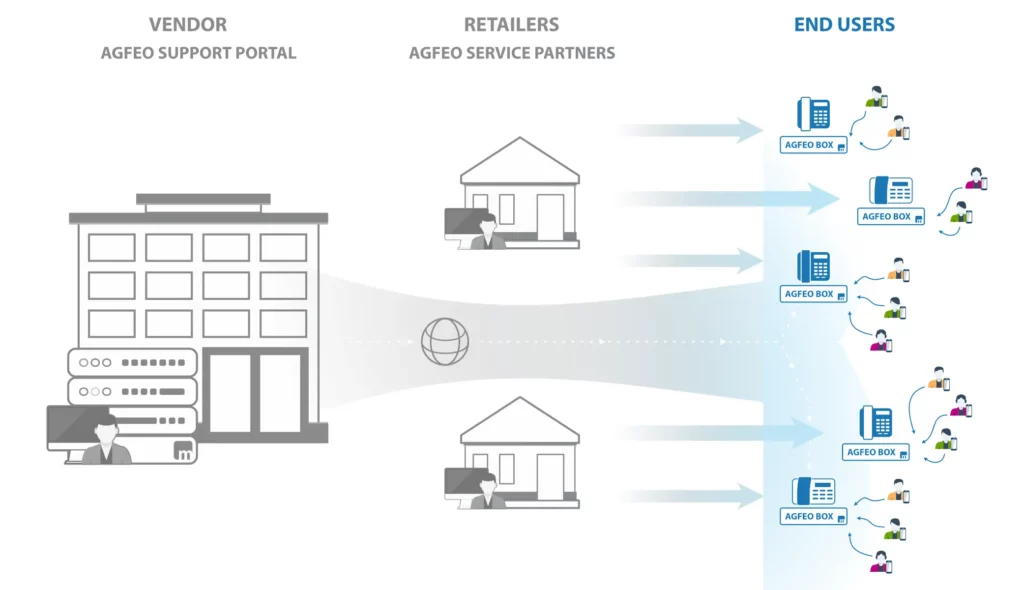
The concept of "IoT access from anywhere" highlights the evolution of technology in connecting us to our homes, offices, and even vehicles, regardless of location. For AGFEO end users, secure remote access for phone end users and their devices is made possible. This enables users to access their own telephony devices securely and conveniently and provides them with a seamless and secure communication system with internal and external users.
Consider the practical implications of such capabilities. For property owners and managers, IoT access control is more than a convenience; it is a fundamental shift in how they manage their assets. The ability to control access, monitor activity, and respond to incidents remotely offers significant advantages. 5G IoT smart access can be used in various settings, including houses, offices, work sites, community facilities, storage spaces, and hotels. Furthermore, it is exceptionally beneficial where there is regular foot traffic, providing an additional layer of security and management capability.
The term "IoT access control" is itself a crucial piece of the puzzle. It's a technique for controlling physical access control components such as doors and locks. This is where technologies such as smart locks, which can be managed via a smartphone app from anywhere with an internet connection, come into play. Beyond residential applications, this technology is transforming how businesses and institutions secure their premises, from offices and factories to data centers and critical infrastructure.
The benefits of IoT access control are numerous and far-reaching, offering advantages to residents, tenants, installers, property owners, and managers. It increases security by allowing remote monitoring, real-time alerts, and the ability to grant or revoke access as needed. It can also streamline operations, offering the potential to reduce labor costs and improve efficiency. And it provides data-driven insights, offering valuable information about property usage and security patterns.
The practicalities of implementing "IoT access from anywhere" are not always straightforward. As with any technology, there are challenges. One of the most significant is security. When devices are connected to the internet, they are vulnerable to cyberattacks. This is why multiple layers of security are necessary, including physical security to protect the devices themselves, network security to protect data transmission, and data security to encrypt and protect sensitive information. Strong passwords, regular software updates, and robust network security protocols are essential. It's crucial to remember that the responsibility for security lies not just with manufacturers, but also with the users and managers of these systems.
Beyond security, another significant hurdle is the underlying infrastructure. The success of "IoT access from anywhere" is heavily reliant on a reliable internet connection. This can be a problem in areas with poor connectivity or where there is no wired access. Satellite access is one solution for areas where mobile services are absent or unreliable, providing a pathway for communication and control in even the most remote environments.
For those looking to implement "IoT access from anywhere," a range of solutions is available. Consider the potential of platforms designed to handle the hardware side of things, allowing you to focus on the application side. Then consider the tools and platforms you already use and love. These tools can often be adapted to easily apply the IoT data you gather. Remote access tools, such as TeamViewer Tensor, offer a way to easily and securely access and manage IoT devices from anywhere. These tools allow you to manage, service, and support your devices remotely, offering the ability to access your IoT's desktop environment remotely with ease, including managing files and running applications.
The concept of remote access extends to industrial applications as well. RemoteIoT allows you to securely connect and manage machines and devices from anywhere, even through firewalls. All network traffic is encrypted via an SSH tunnel, ensuring data security and preventing unauthorized access. With these tools, you can not only control your devices but also monitor them in real-time.
Regardless of the solution chosen, one must consider the core components required for this capability: the IoT devices themselves, a network to connect them, a platform for management and control, and the user interface. These components must work in harmony to deliver a seamless and secure experience. To secure your IoT systems, it is crucial to protect the physical devices from tampering and to protect the network and data. This might seem difficult, but there are simple solutions like choosing secure passwords and keeping your device updated.
The potential for "IoT access from anywhere" is enormous. It is changing the way we interact with technology and reshaping industries. By embracing the principles of security, reliability, and usability, we can harness the power of IoT to create a world that is more connected, efficient, and secure. The future is now, and with the right approach, the ability to control your world from anywhere is within your grasp.
| Aspect | Details |
|---|---|
| Concept | IoT Access from Anywhere |
| Core Functionality | Remote control and monitoring of IoT devices regardless of physical location. |
| Applications | Smart homes, offices, vehicles, industrial machinery, security systems, remote equipment management, etc. |
| Benefits | Increased security, operational efficiency, remote asset management, data-driven insights, convenience for individuals. |
| Key Technologies | Smart locks, remote access tools (TeamViewer Tensor, RemoteIoT), VPNs, centralized dashboards, 5G, satellite access. |
| Security Considerations | Multi-layered security (physical, network, and data), strong passwords, regular software updates, secure network protocols. |
| Infrastructure Requirements | Reliable internet connection, 5G network, satellite access for remote areas. |
| Implementation Considerations | Choosing appropriate platforms, secure hardware, focusing on user-friendly interfaces and device compatibility. |
| Future Implications | Continued growth in smart cities, connected vehicles, and industrial automation. |
| Relevant Technologies |
|
| Examples of Use |
|
| Challenges | Cybersecurity threats, infrastructure limitations (internet access), data privacy concerns, ensuring user adoption, data transfer and storage. |


Detail Author:
- Name : Barbara Kihn DVM
- Username : mathilde16
- Email : zvonrueden@robel.com
- Birthdate : 2007-05-03
- Address : 2116 Weimann Plains Wiegandtown, IN 25271-1200
- Phone : 478-712-2971
- Company : Schuppe, Greenholt and Beatty
- Job : Press Machine Setter, Operator
- Bio : Autem est iusto facilis nisi. Est quia sit et et ex praesentium sapiente. Qui sit eos consequatur id porro numquam. Molestias nobis aut ea esse. Alias non quis nam architecto officiis sint.
Socials
linkedin:
- url : https://linkedin.com/in/ljenkins
- username : ljenkins
- bio : Placeat nihil laboriosam eligendi quam voluptate.
- followers : 5559
- following : 2979
tiktok:
- url : https://tiktok.com/@laurel.jenkins
- username : laurel.jenkins
- bio : Nobis consequuntur iure voluptatem commodi fugiat ipsam corporis.
- followers : 4032
- following : 1610
facebook:
- url : https://facebook.com/laurel_jenkins
- username : laurel_jenkins
- bio : Exercitationem deleniti recusandae iure.
- followers : 1872
- following : 1985
twitter:
- url : https://twitter.com/jenkinsl
- username : jenkinsl
- bio : Consequatur ut sit maxime voluptate impedit hic. Iste at deleniti voluptatibus similique quis. Aut aut atque illo mollitia est ut.
- followers : 818
- following : 1886
instagram:
- url : https://instagram.com/ljenkins
- username : ljenkins
- bio : Suscipit blanditiis odio corrupti vel. Velit odio in cumque qui omnis.
- followers : 2593
- following : 708