Access IoT Devices Behind NAT: Secure Remote Access Guide
Can you truly access your Internet of Things (IoT) devices, nestled securely behind Network Address Translation (NAT) firewalls, from anywhere in the world?
The answer, surprisingly, is a resounding yes, offering a world of possibilities for remote management, monitoring, and control, all while safeguarding your devices from unwanted intrusions. Navigating the complexities of NAT and firewalls can seem daunting, but with the right strategies, you can unlock the full potential of your IoT ecosystem.
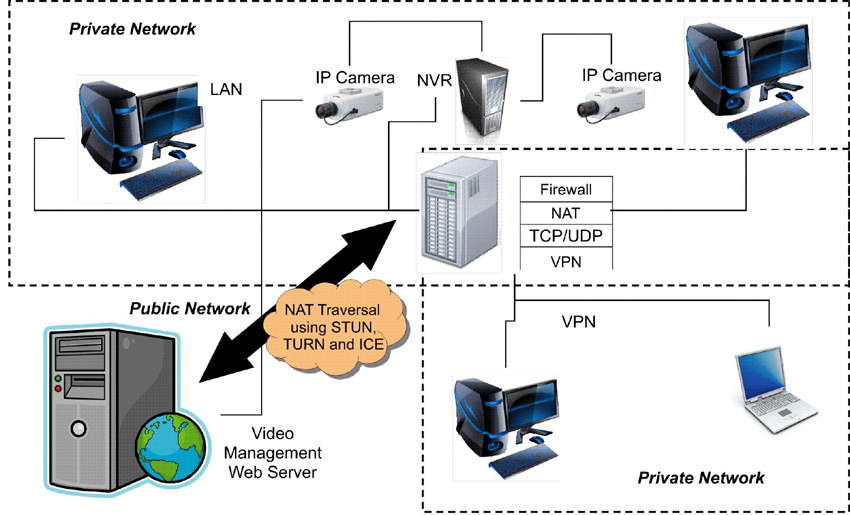
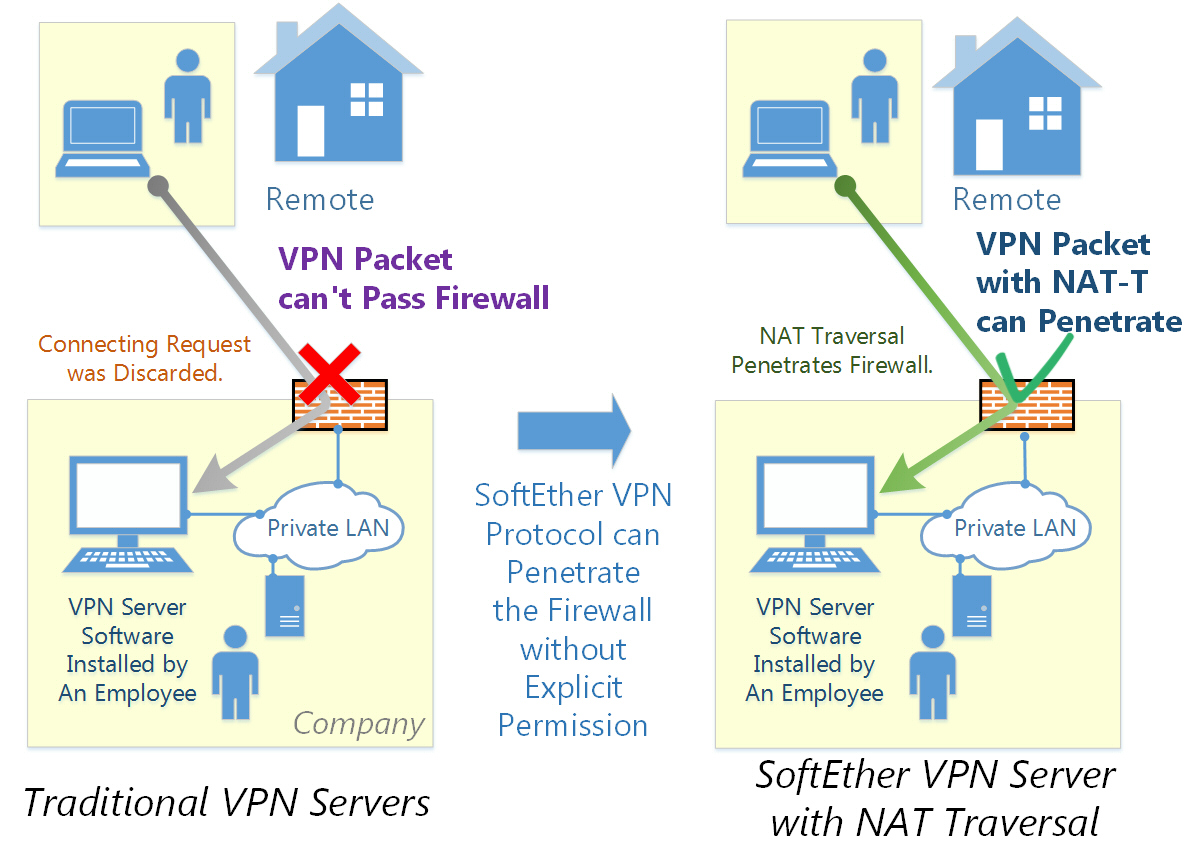
The challenge of accessing IoT devices behind NAT is a well-documented one. NAT, in essence, acts as a security gatekeeper. It translates the private IP addresses of your devices within your local network into a single public IP address, shared by your router. This setup shields your devices from direct external access. Think of it like a club bouncer, only letting in those with the right credentials, and preventing direct entry to the individual patrons inside. This is the essence of what prevents external access, but there are several ways to navigate around it.
- Caitlyn Jenner Sophia Hutchins Relationship Status Revealed Get The Details
- Avoid Search Errors Tips When Google Shows No Results
Internet Service Providers (ISPs) often employ NAT or Carrier-Grade NAT (CGNAT) on their routers, making traditional port forwardinga common method for external accessa complicated and sometimes impossible task. Port forwarding, which involves configuring your router to direct specific incoming traffic to a particular device on your network, can also expose your devices to security vulnerabilities, as it creates an open pathway for potential attacks. So, What are the options?
| Method | Description | Pros | Cons |
|---|---|---|---|
| Reverse SSH Tunneling | Establishes a secure tunnel from the IoT device to a trusted server, allowing you to route traffic through the server to access the device. | Secure, avoids port forwarding, works behind most NAT configurations. | Requires a server with a public IP address, more complex setup. |
| Cloud-Based IoT Platforms | Utilizes platforms like SocketXP to manage, access, and monitor devices behind NAT and firewalls. | Easy to use, offers remote access, and simplifies device management. | Often requires a subscription or payment. |
| SSH Key Authentication with Clients like Putty | Enhances security with secure key authentication, preventing un-authorized access. | Enhanced security, suitable for secure data transfer. | Requires SSH configuration, additional knowledge to setup the solution |
| VNC (Virtual Network Computing) | Provide full desktop access to your IoT devices remotely | Easy configuration, no additional setup required, | Suitable for graphical user interfaces. |
| Pinggy.io | Allows remote access without setting up port forwarding | Simple, efficient, quick setup. | Requires an internet connection |
One of the most effective techniques for accessing devices behind NAT is reverse SSH tunneling. In simple terms, this involves creating an outbound SSH connection from your IoT device to a server with a public IP address. You can then use this tunnel to forward traffic from your local machine through the server and onto the IoT device. The beauty of this method lies in the fact that the IoT device initiates the connection, bypassing the need for router configuration or a public IP address on the device itself. The server acts as an intermediary, allowing you to securely access your device remotely, as if you were connected directly to its local network.
The process starts with setting up the tunnel on the client (your IoT device) first. Tools like Putty on the client side can be utilized for SOCKS proxying. This tunnel then redirects the traffic through the server. The server doesn't need to know the specific IP address of the device. This approach leverages the existing outbound connection to bypass the typical NAT restrictions, making it ideal for scenarios where port forwarding is not possible or desirable.
For instance, consider an MQTT broker within your home network, shielded by your router's NAT. Using reverse SSH tunneling, you can establish a secure, remote connection to this broker from anywhere, allowing you to manage and monitor your IoT devices without the need to expose the broker directly to the internet.
Cloud-based IoT platforms, such as SocketXP, offer another convenient solution. These platforms provide a comprehensive suite of tools for remote device management, including secure access, monitoring, and control. They often incorporate their own tunneling mechanisms, simplifying the setup process and allowing you to manage your devices through a user-friendly web interface. This option is particularly attractive for those who prefer a more streamlined and less technical approach.
SSH key authentication is a critical element of security when accessing devices remotely. It provides a more robust and secure authentication method than simple password-based logins, enhancing the overall security of your IoT devices. Tools like Putty support SSH key authentication. It's a good practice to use SSH key authentication to enhance the security of your connection, preventing unauthorized access to your devices.
When considering remote access, you need to think beyond simple command-line access. Remote desktop solutions like VNC (Virtual Network Computing) offer a full desktop experience, enabling you to interact with your devices as if you were sitting in front of them. This is particularly useful for managing devices with graphical user interfaces, such as Raspberry Pi units running desktop environments.
For those looking for a simple way to establish remote access without complex configuration, services like pinggy.io offer a quick and easy solution. Pinggy creates a temporary tunnel to your device, allowing you to access it via a public URL. This method is particularly helpful for quick tests and temporary access needs.
It's crucial to remember that NAT (Network Address Translation) is like the bouncer at the club. It serves as a gatekeeper, translating private IP addresses to a public IP. This presents a hurdle to directly accessing devices from the outside. Without it, devices would not be able to form meaningful connections to the outside world. It would be impossible to use today's internet services.
Let's consider a real-world example. Imagine you have a web server running on a Raspberry Pi within your home network, with a private IP address. You want to access this web server from anywhere in the world. Reverse SSH tunneling is the perfect solution. You would set up an outbound SSH connection from your Raspberry Pi to a server with a public IP. Then, you can use your local machine to connect to that public server. All traffic is redirected through the secure SSH tunnel, allowing you to access your web server as if it were directly connected to the internet. No port forwarding is needed, keeping your home network secure.
You never assign a domain name to the device that is behind several layers of NAT. You assign it to the device (router) that has the public IP. When you encounter an issue, you may need to troubleshoot by checking spelling or trying a new query. In general, these configurations are the best. They provide a secure and reliable means of accessing your IoT devices from anywhere. It's important to choose the approach that best suits your technical skills, security requirements, and specific use case.
If IoT devices need access to your default subnet initially, consider using firewall rules to restrict access based on specific IP addresses or services. Gradually tightening security is crucial. NAT or virtual IPs are employed for selective WAN access control. Do you have a firewall in between those on the IoT segment or anywhere in your environment?
If not and all devices are behind a NAT router of some sorts, then the IoT devices still have access to everything else in your network, they'll just look like a single IP to the the routers involved. To manage IoT behind a firewall and interact with the internet while disguising their IP addresses, a NAT device may also safeguard IoT appliances. This is something to keep in mind. Cloud-based IoT platforms such as SocketXP is a cloud based IoT device management and remote access platform that helps in this regard.
Whether you're managing a fleet of Raspberry Pis, a private MQTT broker, or any other Linux-based machine behind NAT, the ability to remotely access and control your IoT devices is a game-changer. By understanding the challenges of NAT and the various available solutions, you can create a secure, reliable, and flexible remote access environment, unlocking the full potential of your IoT ecosystem.
The key takeaway? Don't let NAT hold you back. With the right knowledge and tools, you can seamlessly connect to and manage your IoT devices from anywhere, securely, reliably, and without the complexities of traditional port forwarding.

Detail Author:
- Name : Laverne Walter
- Username : marley63
- Email : bergstrom.german@hotmail.com
- Birthdate : 2006-05-06
- Address : 53611 Abshire Crest Alvertachester, NC 82070
- Phone : 773.546.9369
- Company : Schoen, Hand and Marvin
- Job : Farm Equipment Mechanic
- Bio : Dignissimos culpa quia aut blanditiis. Nostrum ad sequi quaerat non tempore aut rerum. Eos illo et soluta aut.
Socials
linkedin:
- url : https://linkedin.com/in/leone_real
- username : leone_real
- bio : Quis aut ab dignissimos earum.
- followers : 6998
- following : 1564
tiktok:
- url : https://tiktok.com/@lgreenfelder
- username : lgreenfelder
- bio : Quis qui ducimus et impedit maiores placeat.
- followers : 2278
- following : 2892