Remote IoT Access: Methods & Security Tips You Need To Know!
Can you truly harness the power of your Internet of Things (IoT) devices from anywhere in the world? The answer is a resounding yes, unlocking unprecedented control and convenience through remote access.
The world of interconnected devices is rapidly expanding, with smart homes, industrial machinery, and countless other applications relying on the seamless flow of data and control. However, the true potential of these devices is often limited by their physical accessibility. Imagine being able to monitor your home security system while on vacation, troubleshoot a factory machine from your office, or simply adjust your thermostat from the comfort of your bed. Remote access to IoT devices makes this a reality, transforming the way we interact with and manage our increasingly connected world. The raspberry pi, for instance, is an amazing computer that can be configured to perform many different projects and applications, however, it has an inconvenient drawback: users must connect a screen, keyboard, and mouse to the pi to use it directly. This article will delve into the mechanics of remote access, exploring various methods and highlighting the benefits and considerations associated with each approach.
Before we proceed, it's beneficial to establish a clear understanding of the core concepts. IoT monitoring, or device management, encompasses a broad spectrum of tasks, including validation, configuration, monitoring, and analysis. This involves equipping and managing diverse IoT devices from a central location. The goal is to provide comprehensive support and functionality for the full spectrum of their capabilities. This is why an effective and secure IoT device management solution is highly valued in the industry. Remote access, at its essence, allows you to connect to and control multiple IoT devices from a remote location. These are usually accessed remotely from a central dashboard. This capability enables users to monitor and manage their IoT devices from anywhere. In practical applications, think of appliances in a smart home, surveillance cameras, or industrial machinery. It offers convenience, efficiency, and peace of mind.
- Downloading Telegram Insights Resources Explore Now
- Sky Cinema Latest Movies Paramount Vue Tickets Deals Guide
Methods for Remote Access to IoT Devices
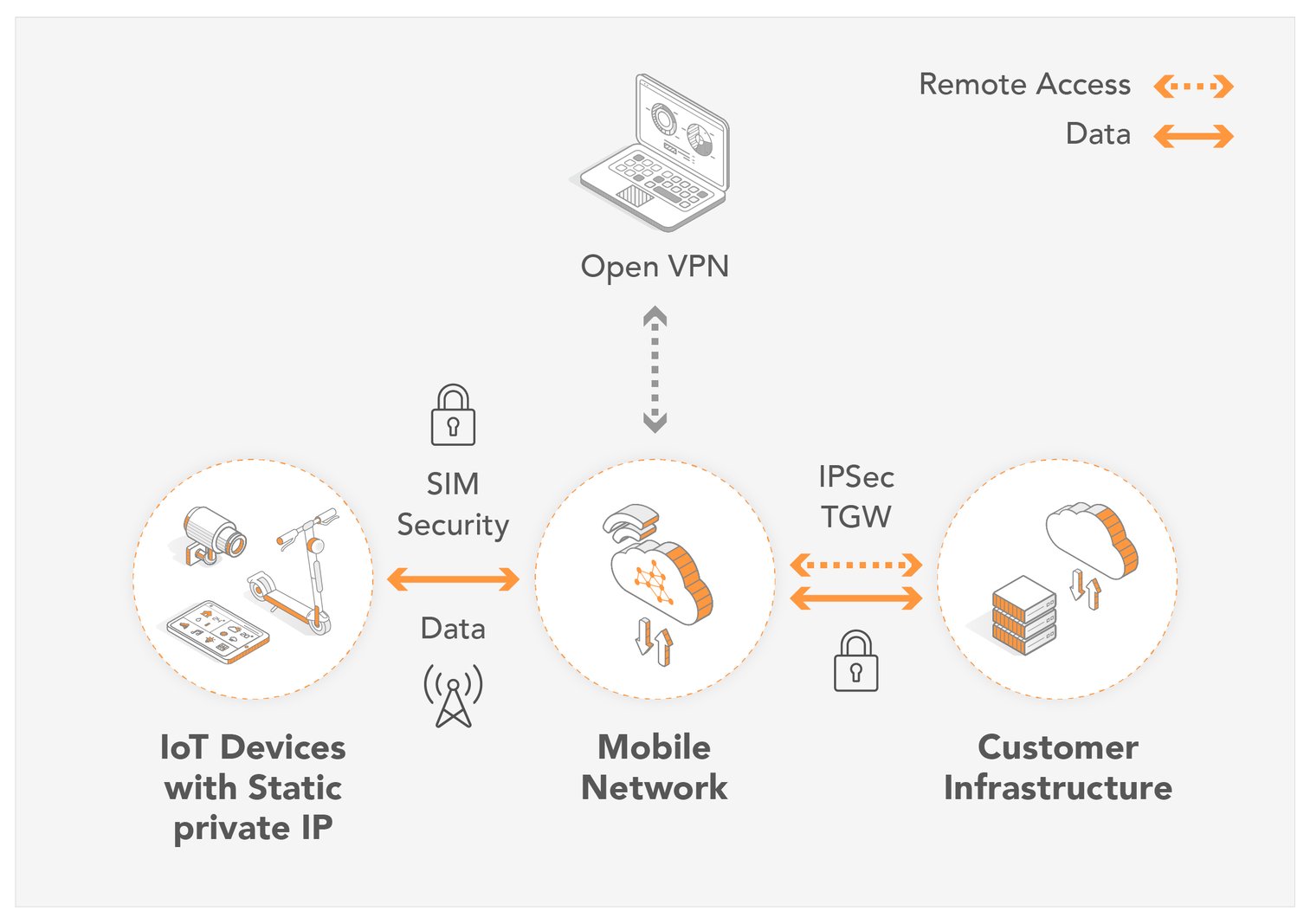
Numerous methods facilitate remote access to IoT devices. Each method has its own set of benefits and drawbacks. The choice of method will depend on the specific needs and requirements of the user. The most common options include:
- SSH Connections: Secure Shell (SSH) provides a secure channel for remote access. This method is often used for command-line access and is particularly useful for devices like the Raspberry Pi.
- VPN Connections: Virtual Private Networks (VPNs) create a secure, encrypted connection to a remote network. VPNs are a popular choice in industrial settings due to their robust security features.
- Proxy Connections: Proxy servers act as intermediaries, forwarding network requests to the IoT device. This can be useful for accessing devices behind firewalls or NAT routers.
- RDP Connections: Remote Desktop Protocol (RDP) allows users to access the graphical user interface (GUI) of a remote device.
Many of these methods involve setting up secure tunnels to allow for safe transfer of data between the user and the IoT devices. Another method includes port forwarding (direct access via public IP).
The Significance of Secure Remote Access
The importance of securing remote access to IoT devices cannot be overstated. Given the increasing prevalence of these devices across various environments homes, offices, factories security becomes paramount. In professional or industrial settings, where devices handle sensitive data or require direct remote access, VPNs are frequently used. IT professionals leverage VPNs to securely access IoT devices on remote networks. The use of secure tunneling is a feature of AWS IoT device management that facilitates secure remote access managed by AWS IoT. Secure tunneling does not require updates to inbound firewall rules, maintaining the existing security level. Secure remote access protects against unauthorized access, data breaches, and other security threats. This not only protects sensitive data but also ensures the ongoing functionality and reliability of the IoT devices.
Case Study
One notable solution for remote access is SocketXP, a cloud-based service. SocketXP allows SSH access to remotely located IoT devices such as a Raspberry Pi, Arduino, or Nvidia Jetson, even those behind NAT routers or firewalls. SocketXP employs secure SSL/TLS VPN tunnels. This goes beyond screen sharing and extends to terminal access, app control, and edge management, providing a comprehensive solution for complex IoT management scenarios. With its advanced features and ease of use, SocketXP simplifies remote access, allowing users to manage devices without the complexities of network configurations.
Remote access has revolutionized the way we interact with and manage our devices. The ability to control and monitor IoT devices from anywhere offers convenience, efficiency, and peace of mind. Remote access allows users to interact with these devices over the internet or through specific network protocols. Hey there tech enthusiasts, lets dive straight into the deep end of a common issue thats got a lot of mac users pulling their hair out. These devices help automate processes, improve efficiency, and give you more control over your environment. Before diving into the details, lets get a clear understanding of what remote access to iot devices really means. At its core, remote access enables you to manage and control iot devices through the internet.
Addressing a Common Challenge
The Raspberry Pi, a compact and versatile computer, is a favorite among hobbyists and professionals alike. However, its usability is initially limited by the need for a direct connection (screen, keyboard, and mouse). Remote access overcomes this limitation by allowing users to interact with the Pi from any location. The advantages are clear; one can monitor the Raspberry Pi from a central dashboard, allowing users to interact with these devices over the internet or through specific network protocols. This allows users to remotely manage projects, debug code, and make changes without physical presence. This same challenge and solution apply to other similar embedded systems, such as Arduino and Nvidia Jetson.
The Future of IoT and Remote Access
The future of IoT is inextricably linked to the evolution of remote access technologies. As the number of connected devices continues to grow exponentially, the need for secure and efficient remote management will only increase. Innovations in cloud computing, edge computing, and cybersecurity will play a crucial role in shaping the future of remote access. We can expect to see more sophisticated solutions, such as AI-powered device management platforms and enhanced security protocols, further streamlining the remote access experience. The internet of things (iot) is transforming the way consumers and customers interact with the physical world. In smart homes, smart retail, and smart factories, iot devices enable us to monitor, control, and optimize various aspects of our personal lives, business operations, and manufacturing processes.
Considerations and Best Practices
While the advantages of remote access are compelling, certain considerations are essential for a successful implementation. Security is paramount. Users should implement robust authentication mechanisms, encryption, and regular security audits. Furthermore, users should consider the bandwidth requirements of remote access. Streaming video or large data transfers require adequate internet connectivity. Proper network configuration is also critical. This includes setting up firewalls, port forwarding, and VPN connections. By adhering to these best practices, users can unlock the full potential of their IoT devices while minimizing security risks.
To access your Windows IoT Core device over the internet, you can set up remote access by configuring your network and the device properly.
The significance of secure remote access for iot devices cannot be overstated. It enhances the safety and usability of the devices. The significance of secure remote access for iot devices cannot be overstated. It enhances the safety and usability of the devices.
The internet of things (iot) is transforming the way consumers and customers interact with the physical world. With iot devices spread across various environmentshomes, offices, factories, and moreremote access allows users to interact with these devices over the internet or through specific network protocols.
In Summary
Remote access to IoT devices has revolutionized how we interact with our connected world. It provides unparalleled convenience, efficiency, and the ability to manage and monitor devices from any location. By understanding the various access methods, prioritizing security, and implementing best practices, users can fully harness the transformative power of remote access, opening new possibilities in smart homes, industrial automation, and countless other applications.


Detail Author:
- Name : Violette Romaguera I
- Username : mbergstrom
- Email : ledner.shakira@medhurst.com
- Birthdate : 1983-01-23
- Address : 562 Sim Lock Suite 966 Jonesshire, MD 08285
- Phone : 740-626-6433
- Company : Casper-Champlin
- Job : Civil Drafter
- Bio : Autem autem neque est nostrum. Enim quasi asperiores tempora asperiores quo. Nostrum fuga nobis nulla debitis cum earum. Ut dolore nobis quam voluptates eum distinctio.
Socials
instagram:
- url : https://instagram.com/walton_dev
- username : walton_dev
- bio : Non omnis numquam quod facilis. Commodi est consectetur occaecati.
- followers : 4113
- following : 895
twitter:
- url : https://twitter.com/walton_dev
- username : walton_dev
- bio : Hic facere natus voluptatem beatae animi. Tenetur sequi quis eaque deserunt in tempore optio in. Sed voluptas eveniet et sint dolor veritatis.
- followers : 5039
- following : 2330