Accessing IoT Behind Router: Your Ultimate Guide & Best Practices
Can you imagine a world where your home, your office, your entire life, is accessible at your fingertips, no matter where you are? The ability to remotely access and control your Internet of Things (IoT) devices behind a router isn't just a futuristic fantasy; it's a present-day reality, empowering individuals and businesses with unprecedented control and convenience.
The integration of IoT devices into our lives has exploded, transforming everything from how we manage our homes to how businesses operate. Smart thermostats, security systems, industrial sensorsall designed to enhance efficiency and provide valuable dataare now commonplace. However, the true potential of these devices is unleashed when you can access and control them remotely, especially when they are nestled behind the protective shield of a router. But, how do we accomplish this while ensuring our networks remain secure?
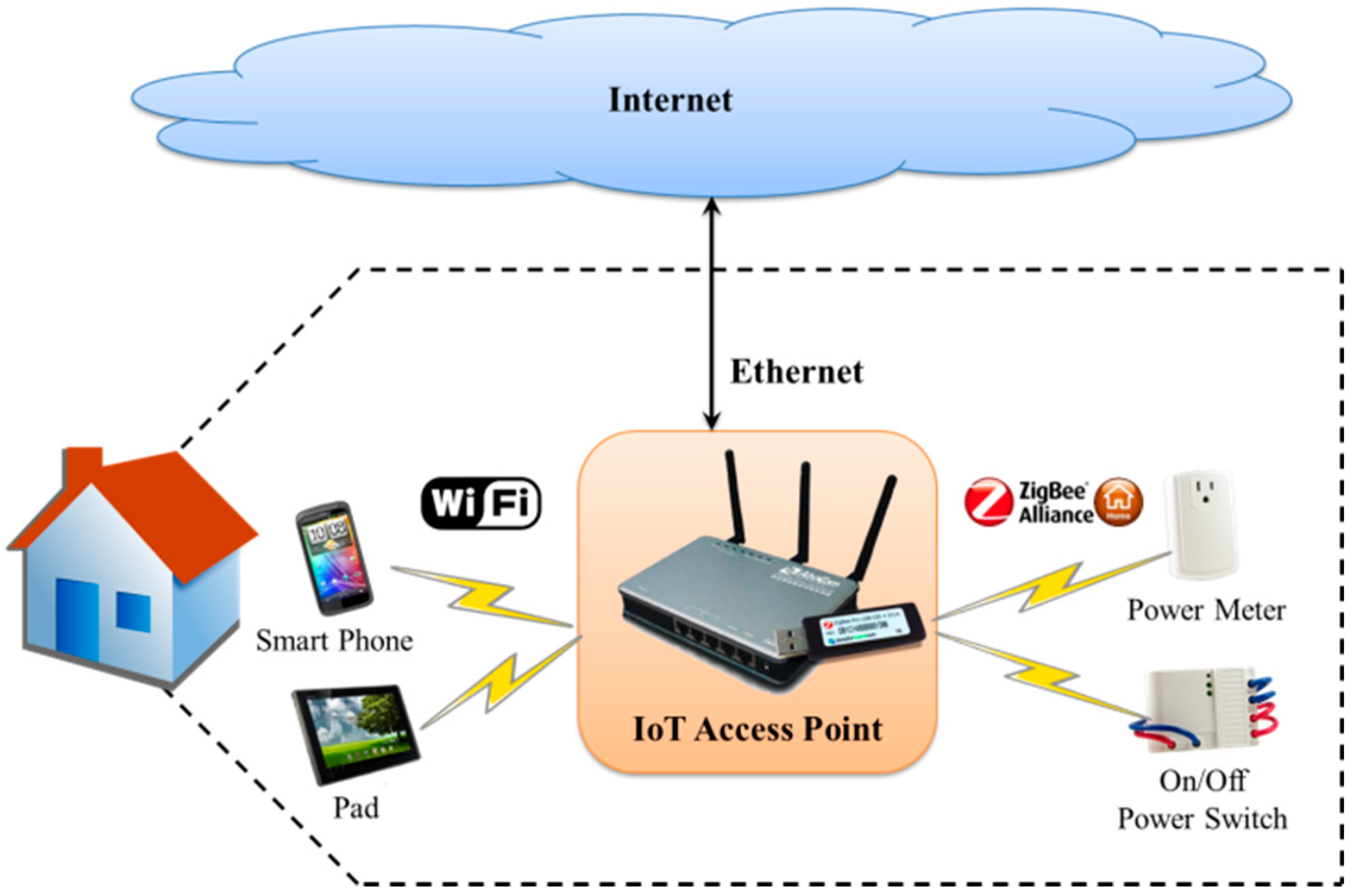
Routers, the unsung heroes of the digital age, play a pivotal role in the functioning of IoT networks. They act as gatekeepers, managing the flow of data traffic and facilitating secure communication between your devices and the outside world. Understanding how a router functions within an IoT ecosystem is critical to gaining effective remote access.
- Kannada Movies 2023 Your Ultimate Guide To Releases Best Films
- Unanswered Amy Carters Husband No Results Find Out
Now, let's break down the core aspects of securing remote access to your IoT devices:
Understanding Your Router's Role
Your router, acting as an intermediary, manages the communication between your local IoT devices and the external network (the internet). Its primary functions include:
- Kannada Movies 2023 Releases Reviews Where To Watch
- India Streaming Guide Luxmovieslive Insights Find Out Now
- Network Address Translation (NAT): This allows multiple devices on your local network to share a single public IP address, enhancing security by masking the internal IP addresses of your devices.
- Firewall: The router's built-in firewall scrutinizes incoming and outgoing network traffic, blocking unauthorized access and potential threats.
- Data Routing: Directing data packets between devices on your local network and the internet.
Why Accessing IoT Behind a Router is Important
Remote access opens up a world of possibilities:
- Convenience: Control your smart home devices from anywhere adjust the thermostat, unlock doors, check security cameras, and more.
- Efficiency: Monitor and manage industrial equipment, servers, and other critical devices remotely, minimizing downtime and improving operational efficiency.
- Troubleshooting: Remotely diagnose and fix issues with your IoT devices, reducing the need for on-site visits.
- Monitoring: Keep track of your devices' performance.
Port Forwarding: Opening the Gate
Port forwarding is the process of configuring your router to allow incoming connections to specific devices on your local network. It's like creating a direct pathway through the router's firewall.
How it Works
- Port Number: Each application or service on your IoT device listens on a specific port number (e.g., 80 for HTTP web traffic, 22 for SSH).
- Configuration: You specify the port number, the internal IP address of the IoT device, and the protocol (TCP or UDP) in your router's settings.
- External Access: When an external device attempts to connect to your public IP address and the specified port, the router forwards the connection to the corresponding IoT device on your local network.
Dynamic DNS: Keeping Track of Your Address
Your public IP address, assigned by your internet service provider (ISP), is typically dynamic, meaning it can change periodically. This presents a challenge for remote access, as you need a way to always know the current IP address. Dynamic DNS (DDNS) services solve this problem.
How it Works
- DDNS Provider: You sign up for a DDNS service (e.g., No-IP, DynDNS).
- DDNS Client: You install a client on your network (often built into the router) that monitors your public IP address.
- Automatic Updates: Whenever your IP address changes, the client automatically updates the DDNS service with your new address.
- Domain Name: You are assigned a unique domain name (e.g., myiotdevices.example.com).
- Remote Access: You can use your domain name to access your IoT devices, regardless of the underlying IP address changes.
VPN: The Secure Tunnel
A Virtual Private Network (VPN) provides a secure, encrypted connection between your device and your local network. It's like creating a private tunnel through the internet.
How it Works
- VPN Server: You set up a VPN server on your router or on a device within your local network (e.g., a Raspberry Pi).
- VPN Client: You install a VPN client on your remote device (e.g., your phone or laptop).
- Secure Connection: The client connects to the VPN server, establishing an encrypted tunnel.
- Access to Local Network: Once connected, your remote device is assigned an IP address on your local network, allowing you to access your IoT devices securely.
Setting Up Remote Access
The process involves several steps, detailed here:
- Choose a Method: Port forwarding or VPN, each with its pros and cons. Port forwarding is simpler, while VPN is more secure.
- Configure Your Router: Access your router's administration panel (usually through a web browser) and configure port forwarding or set up the VPN server.
- Set Up Dynamic DNS (If Using Port Forwarding): Sign up for a DDNS service and configure the client.
- Configure Your IoT Devices: Assign static IP addresses to your IoT devices to avoid IP address conflicts.
- Install a VPN client on the remote devices.
- Test the Connection: Verify that you can access your IoT devices from outside your local network.
Security Tips for IoT Devices Behind a Router
Protecting your network and devices is paramount:
- Strong Passwords: Use strong, unique passwords for your router, IoT devices, and all related accounts.
- Regular Updates: Keep your router's firmware and the firmware of your IoT devices up to date to patch security vulnerabilities.
- Enable Firewall: Ensure the firewall on your router is enabled.
- Disable Unnecessary Services: Disable any services on your router or IoT devices that you don't need.
- Isolate IoT Devices (Optional): Consider creating a separate VLAN (Virtual LAN) for your IoT devices to isolate them from your primary network.
- Monitor Network Traffic: Regularly monitor your network traffic for suspicious activity.
- Use Multi-Factor Authentication (MFA): Enable MFA on your router's administration panel and on your remote access accounts.
- Choose Reputable Devices: Purchase IoT devices from reputable manufacturers with a good track record of security.
Remote SSH Access for IoT Devices
Secure Shell (SSH) is a protocol that allows secure remote access to devices through an encrypted channel. It's a vital tool for managing and troubleshooting IoT devices. Setting up remote SSH access typically involves these steps:
- Enable SSH on the IoT Device: Most Linux-based IoT devices (like Raspberry Pi) have SSH enabled by default or can be easily enabled.
- Configure Port Forwarding: In your router settings, forward the SSH port (typically port 22) to the internal IP address of your IoT device.
- Use a Dynamic DNS Service (Optional): If you have a dynamic IP address, use a DDNS service to make sure you can always find your device.
- Access Remotely: Use an SSH client (like PuTTY on Windows or the terminal on macOS/Linux) to connect to your device using your public IP address or DDNS domain name and the SSH port.
Android Device Considerations
Accessing IoT devices behind a router using an Android device requires careful setup and often involves using dedicated apps or tools.
- SSH Clients: Many Android SSH clients are available in the Google Play Store (e.g., JuiceSSH, Termius).
- VPN Clients: Use an Android VPN client to connect to your home network VPN.
- Web Access: If your IoT device has a web interface, you can access it through a browser on your Android device.
Remote Access Solutions
Many companies offer remote access solutions designed for IoT devices, with options suitable for various needs and skill levels.
- SocketXP: A popular choice.
- Teltonika: Ideal for remote management
- TeamViewer: Offers remote access
Steps to Configure Remote Access
The process is relatively straightforward, but varies based on the method you use:
- Make a list of all devices you want to access remotely.
- Choose the right Method: Decide between port forwarding, VPN, or a remote access solution.
- Configure the Router: Set up port forwarding or a VPN server, and enable the DDNS service (if you choose port forwarding).
- Configure the Devices: Set up static IP addresses and enable remote access protocols (SSH, HTTP, etc.) on your devices.
- Test and Secure: Test the connection and secure your network and devices.
Conclusion
In conclusion, Remote access to your IoT devices behind a router opens up a world of possibilities, but it requires a carefully planned approach. By understanding your router's role, mastering techniques like port forwarding and VPNs, and adopting robust security measures, you can unlock the full potential of your connected devices while keeping your network secure. Remember to always prioritize security, stay informed about the latest threats, and adapt your approach as the world of IoT continues to evolve.


Detail Author:
- Name : Keely Ullrich
- Username : brent.bechtelar
- Email : maximus.powlowski@padberg.com
- Birthdate : 1992-05-22
- Address : 531 Gutmann Dam Apt. 803 East Titusfurt, FL 05034-1948
- Phone : 1-260-998-6688
- Company : Murphy-Kuhic
- Job : Forensic Investigator
- Bio : Et eum eos minus impedit sit. In eum ad dolores. Iste impedit quia culpa quia.
Socials
twitter:
- url : https://twitter.com/hettiebogan
- username : hettiebogan
- bio : Quod laborum libero vitae reprehenderit molestias sint dolore sint. Sed consequatur omnis vitae nesciunt aut quo. Nam fuga autem dolores ut.
- followers : 6800
- following : 2212
linkedin:
- url : https://linkedin.com/in/hettie.bogan
- username : hettie.bogan
- bio : Quae enim temporibus voluptatibus beatae quae.
- followers : 4767
- following : 754
facebook:
- url : https://facebook.com/hettie818
- username : hettie818
- bio : Et et similique nulla. Quia ut vel distinctio excepturi facilis natus aliquid.
- followers : 255
- following : 2510
tiktok:
- url : https://tiktok.com/@hettiebogan
- username : hettiebogan
- bio : Cum repellendus labore dolorem in.
- followers : 4487
- following : 1165
instagram:
- url : https://instagram.com/hettiebogan
- username : hettiebogan
- bio : Sed temporibus est officiis voluptates excepturi. Sed non quam et.
- followers : 6485
- following : 418